On-Premise SIEM vs. Cloud-Native Comparison
In recent years there has been a shift within the SIEM landscape with regards of the focus of monitoring not only on-premise devices but also those devices and services in the cloud. This shift has created a need for SIEM solutions to be either on-premise and partially in the cloud (collector in the cloud) or fully in the cloud (cloud native SaaS SIEM solutions). In this article I want to shine light on the differences of on-premise and Cloud native SIEM's and specifically have a closer look at the most forth coming of cloud native SIEM solutions "Microsoft Azure Sentinel".
Comparison table between On-Premise SIEM and Cloud Native SIEM.
| On-Premise SIEM | Cloud Native SIEM | |
| Maintainability | OS Patches are generally behind, Application updates generally mean: log collection interruption. | Network, OS, Application Updates handled by Vendor with minimized collection interruption. |
| Scalability | On-premise vendors nowadays can scale (this was not always the case) but require additional investment/effort. | Scalability is not limited in a cloud environment and happens generally without customer effort. |
| Modifiability | Depending on which vendor you have there are varied degrees of customization that can be applied on the solution. | Due to the SaaS nature of the solution, custom modifications are limited which might not be desirable for every user. |
| Usability | This is hard to generalize on and depends on the solution. (ArcSight generally is more complex, while QRadar is more simplistic) | Simplicity is the trend among cloud solutions, thus cloud native SIEM solutions tend to be easy to use. |
| Performance | Generally when the SIEM was maxed on EPS, using the tool became slower for querying and correlating data. | Collection of logs should not impact correlation limitations as the technology sits on a larger cloud platform that auto-scales. |
| Portability | Data Portability from one SIEM to another has always been near impossible due to different formatting and database types. | This will stay the same as databases and formatting vary in the cloud. |
| Interoperability | Well developed API's are not consistently found among all SIEM vendors, integration generally also depends on popularity and market share of the solution. | Cloud services have a API-Centric architecture causing them easily to integrated with fellow cloud services within and sometimes also outside the vendor's cloud environment. |
| Testability | Testing of performance is common for on premise SIEM solutions and tools are available to test them. | Generally performance is an issue that is owned by the cloud vendor thus not relevant for the end-user to test. |
| Confidentiality | Varies per SIEM vendor, but encryption in transmission, log obfuscation and encryption at rest are found in most SIEMs. | Generally it is recommended not to send sensitive log information into the cloud, if one does data encoding of some sorts needs to take place on the send data. |
| Availability | High Availability capabilities have varied levels of quality among vendors and some even still have log collection interruption with fail-over takes place unless a very complex HA setup is considered. | Due to the nature of SaaS design, high availability comes by design and high SLA rates are generally promised. |
| Integrity | Generally log data integrity is possible with hashing on the SIEM database depending per vendor. | Integrity safeguards are generally a service provided by the cloud vendor but not controlled by the customer. |
| Auditability | Generally most SIEM vendors have relatively detailed audit records on the SIEM application. | Every action done on the system is recorded in an API record allowing for detailed auditability of every action on the solution. |
Critical Highlights when using a cloud native SIEM.
- There will probably be no log data portability within the native cloud
- Content portability might be made partially possible with SOC Prime's Tool to convert content
- Putting extended trust in the vendor since the customer has no access to the backend or the physical machines he puts most of his trust in SOC2/3 certifications and assurance from the vendor.
- Forced upsell other SaaS services of the same vendor might require a license upgrade to be able to offer the full log data content ingested to the cloud native SIEM. This might push costs up significantly.
- Limitation of administrative configuration due to it's SaaS nature the solution might not serve your wide range of security use cases.
- You need to be aware on what type of data you are sending to the cloud and in which cloud region (PII, or other sensitive data types) to avoid compliance violations.
- Masking, Obfuscation, Anonymization, and Tokenization will be key methods to control the data you send and secure into the cloud.
- Vendor lock-in The more you will integrate, the more mature the content and the more you use other services of the same vendor the more you become locked-in the specific cloud provider.
- You don't know actually where your data is residing at any point of time within the cloud.
Advantages when using a cloud native SIEM
- Patching and updates happen automatically (you're never behind patching).
- High availability and scalability is assured.
- General data-center security is of high quality (for the major vendors at least).
- Price per usage allows for quickly scaling out or scaling down to reduce costs.
- Insight in your actual usage cost per period.
Conclusion - Cloud Native SIEM
The cloud native SIEM market is growing rapidly, it has alot of pro's and some con's. It also requires the users to be much more mindful on what type of data will be send to the SIEM. Bottom line: it's not for everybody but it is definitely a new evolution of SIEM.
Closer look at Microsoft Azure Sentinel
Within the cloud market there are currently 3 major players (yes there are other but for this analysis I've focused on the top 3). Each have a form of cloud-native SIEM proposition.
- Amazon AWS - Security Hub (If you google "AWS SIEM" you sometimes also get ELK Stack or detective)
- Google Cloud - Chronicle Backstory (there is limited information available on this solution)
- Microsoft Cloud - Azure Sentinel (most forth coming SIEM player of the 3)
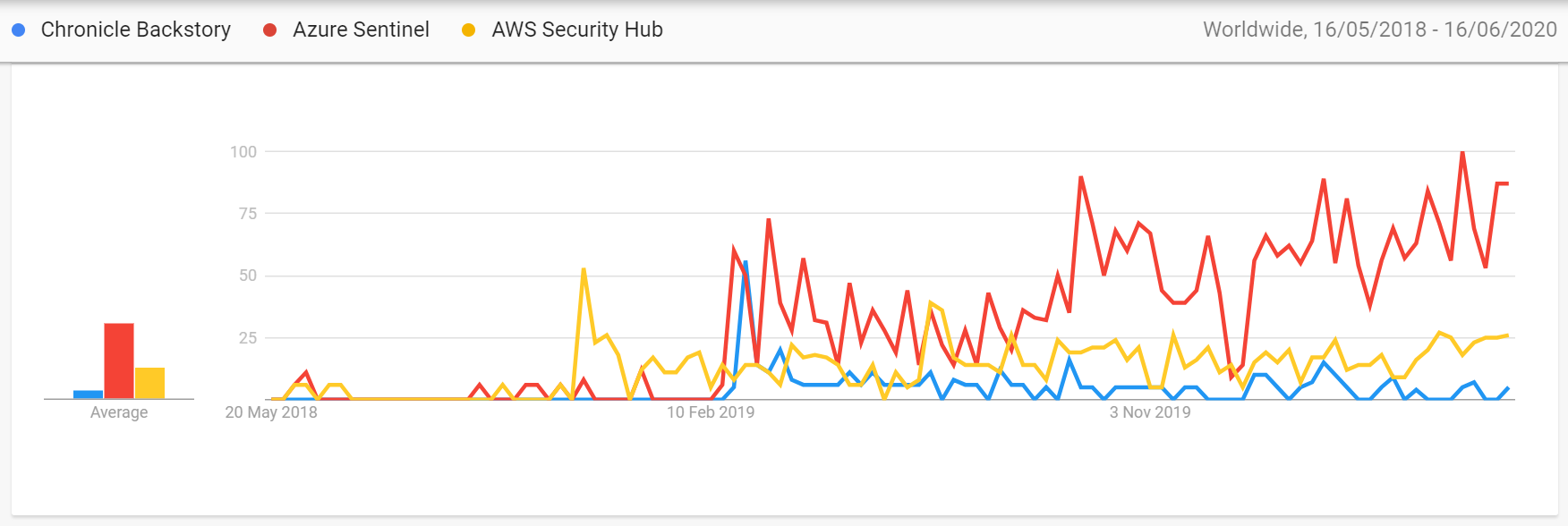
Doing a simple google trends query results shows the following results:
Since Azure sentinel was the most forth coming of the three vendors and had the most easily accessible information available of the three I've taken a closer look at Microsoft Azure Sentinel.
When getting into a new product it's handy to make an overview of available resources for the use of this solution. Similar like I've done for other vendors in the past like in this article.
Documentation - https://aka.ms/asi_documentation
Youtube - https://www.youtube.com/channel/UCGTUbqE3SJiLgtvWjIkSQuQ
Webinars - https://aka.ms/SecurityWebinars
Free Training - https://aka.ms/SentinelNinjaTraining
Conference - https://techcommunity.microsoft.com/ (ignite recap 2019)
Product Blog - https://aka.ms/azuresentinelblog
Content Development - https://github.com/Azure/Azure-Sentinel
Support - https://aka.ms/AzureSentinelMicrosoft
Feature Reqs - https://feedback.azure.com/forums/920458-azure-sentinel
Trial Version - https://azure.microsoft.com/en-us/services/azure-sentinel/
User Community - https://aka.ms/AzureSentinelCommunity
Reddit Community - https://aka.ms/AzureSentinelReddit
Twitter - https://aka.ms/AzureSentinelTwitter
LinkedIN - https://aka.ms/AzureSentinelLinkedIn
Telegram User Chat Groups - https://t.me/AzureSentinelSIEM / https://t.me/AzureSentinelSIEMFEED
With some SIEM vendors in the past information was not always available in each category, in this case there is information freely available for every aspect of this categorization. This shows a open and sharing attitude towards its user community (similar like in the QRadar community).
Before I dive in to my findings on the solution I need to highlight that:
- I've analyzed this through a ArcSight, QRadar (and a bit of Splunk/ELK) background
- I did the Azure Sentinel Level 400 Ninja self study training found here
- I ran a trial instance of Azure Sentinel where I created 1 log source, 1 rule, 1 dashboard, 1 report, 1 automation based on this 1 log source to gain practical experience
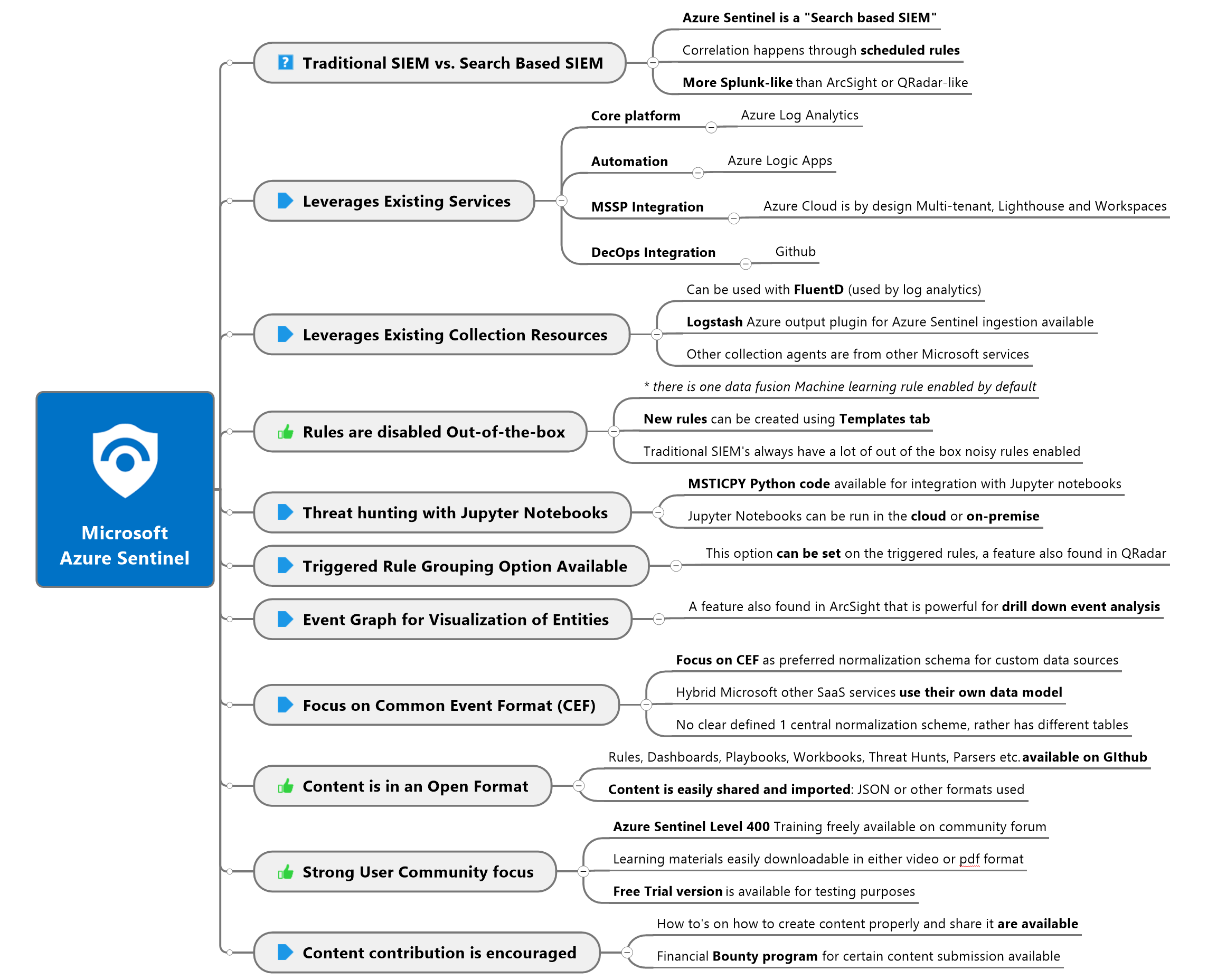
This is not a complete list, but a initial impression of findings thus far.
Conclusion - Azure Sentinel
Microsoft Azure Sentinel has not been existence as long as the on-premise solutions but they have made big steps forward within a short period of time by leveraging existing Microsoft services, open source software like logstash, fluentD and the existing CEF format for ingestion of logs. Although still in it's early maturity stage, thus far it looks as the most promising of the three cloud vendors.