RedSocks Malware Threat Detector with Arcsight SIEM
RedSocks released a Malware Threat Detector appliance which uses netflow in correlation with Threat intelligence feeds and Heuristic patterns (Detection Only/IDS). I hooked it up on a Arcsight SIEM environment and build a flexconnector for it. Now i'll show a few fun things you can do with the information coming out of this appliance. More information about the appliance can be found at the following website: http://www.redsocks.nl/en/.
The goal of this article is to show the added value from ArcSight to a Netflow IDS system. These are the following points Arcsight brings to the table.
- Retention - Arcsight can keep the logs for a very long period.
- Workflow - Using real-time channels to take action on events.
- Analyis - Arcsight has alot of analysis tools inside its framework for doing a in-depth analysis of alerts.
- Dashboarding - Using dashboards for analysis and finetuning of the IDS.
- Advanced correlation - Using other event sources to correlate with IDS events.
Use cases
When you want to get something useful out of a SIEM, start with the use cases.
- Alerts - Real Time Security Intelligence
- Malware activity Detected
- Tor Activty Detected
- Cryptocurrency Mining activty Detected
- Trojan Activty Detected
- Dashboards - Weekly monitoring and analysis
- Top 25 High Severity Alerts
- Top 25 Alerts by Name
- Core network model based on network heuristics
- Geographical Geofence/bad Neighbourhood Dashboard
- Reports - Monthly review
- Top 25 High Severity Alerts
The following table is used to map RedSocks output to output types in the SIEM.
|
RedSocks Alerting Categories |
SIEM Configuration |
|
Very High Risk detection |
|
|
|
|
|
Botnet Controller |
Real-time Alerting |
|
Tor Network |
Real-time Alerting |
|
|
|
|
High Risk detection |
|
|
|
|
|
Mining Pool |
Real-time Alerting |
|
Miscellaneous |
Real-time Alerting |
|
Bad Internet Neighbourhood |
Dashboards/Reports |
|
|
|
|
Medium Risk detection |
|
|
|
|
|
Cloud Storage Service |
Dashboards/Reports |
|
Filesharing Tool |
Dashboards/Reports |
|
Infected Client |
Dashboards/Reports |
|
Instant Messaging |
Dashboards/Reports |
|
Public Proxy |
Dashboards/Reports |
|
Remote Administration |
Dashboards/Reports |
|
Sinkhole |
Dashboards/Reports |
|
|
|
|
Low Risk detection |
|
|
|
|
|
Geofence |
Dashboards/Reports |
|
|
|
|
Heuristic Detection |
|
|
|
|
|
Longlasting connections |
Dashboards |
|
High connection count to same ip but different ports |
Dashboards |
|
Periodic requests to port |
Dashboards |
|
High connection count to same port but different IPs |
Dashboards |
|
Periodic requests to ip |
Dashboards |
|
High connection count to ip, port |
Dashboards |
|
UDP then TCP connections |
Not used |
|
Outgoing ICMP Ping |
Not used |
Flex Connector
I have build a Syslog subagent Flex Connector for Arcsight SIEM which can be downloaded here:
ArcSightRedSocksFlexConnectorParser.zip (This contains the RedSocks.subagent.sdkrfilereader.properties file)
This parser has also the following instructions:
- Setup RedSocks Syslog To send to a ArcSight Smartconnector
- Setup RedSocks Audit Policy
- Install the Parser into a Syslog SmartConnector
Incoming Parsed Logging
Once the logging comes into the Arcsight SIEM, it looks like this:
Note: Source and destination addresses are censored
Note2: The traffic used in the screenshots is sample data
Finetuning the IDS
When you first activate the RedSocks appliance on the network, it will deliver alot of false positives. Here are a few finetune tips:
- The Arcsight SmartConnector does a DNS lookup on every IP received by the RedSocks Appliance, which in turn will create traffic to that specific IP, which triggers the RedSocks again.
- If you have an E-mail server in your network if will do a DNS lookup to a spam server everytime it receives a spam e-mail. which will trigger the RedSocks appliance.
- White list your used DNS servers.
- There will be alot of incoming rat (remote access tool) messages because outside scanners are trying to connect on port 22 (SSH) this will trigger the RedSocks appliance.
- Outgoing traffic to untrusted addresses is more interesting then incoming traffic which is mostly always blocked (if you have a good firewall configuration).
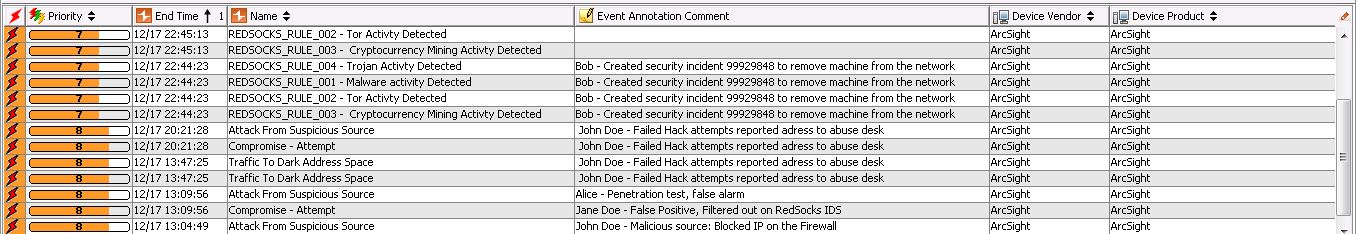
Note: Arcsight SIEM default ruleset will trigger on certain combinations of the incoming events on event category /suspicious
Rules
Here you can see a scenario where multiple rules have been set off by RedSocks events, these events get monitored by the SOC and get commented on per event. Arcsight has a relatively advanced case management system to manage triggered events and fascilitating the analysts workflow.
Dashboards
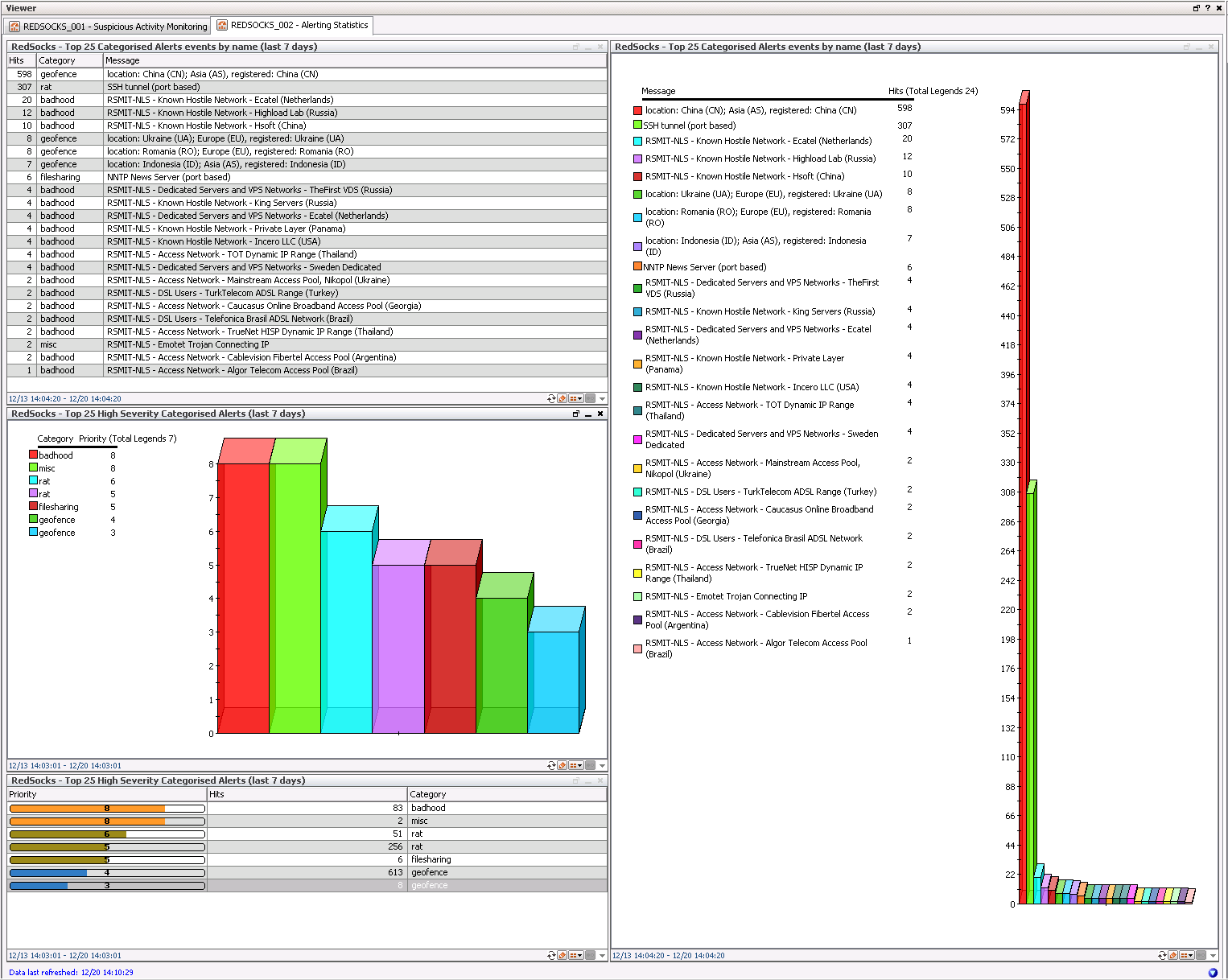
Here you can see the Geographical Geofence/bad Neighbourhood Dashboard the main use case for is traffic analysis and IDS finetuning. Geofence alerts are triggered when a system has a connection with a system falling into the geofence countries defined by the RedSocks appliance. Same goes for Bad neighbourhood traffic which are IP blocks known for having providers which do not regulate their users.
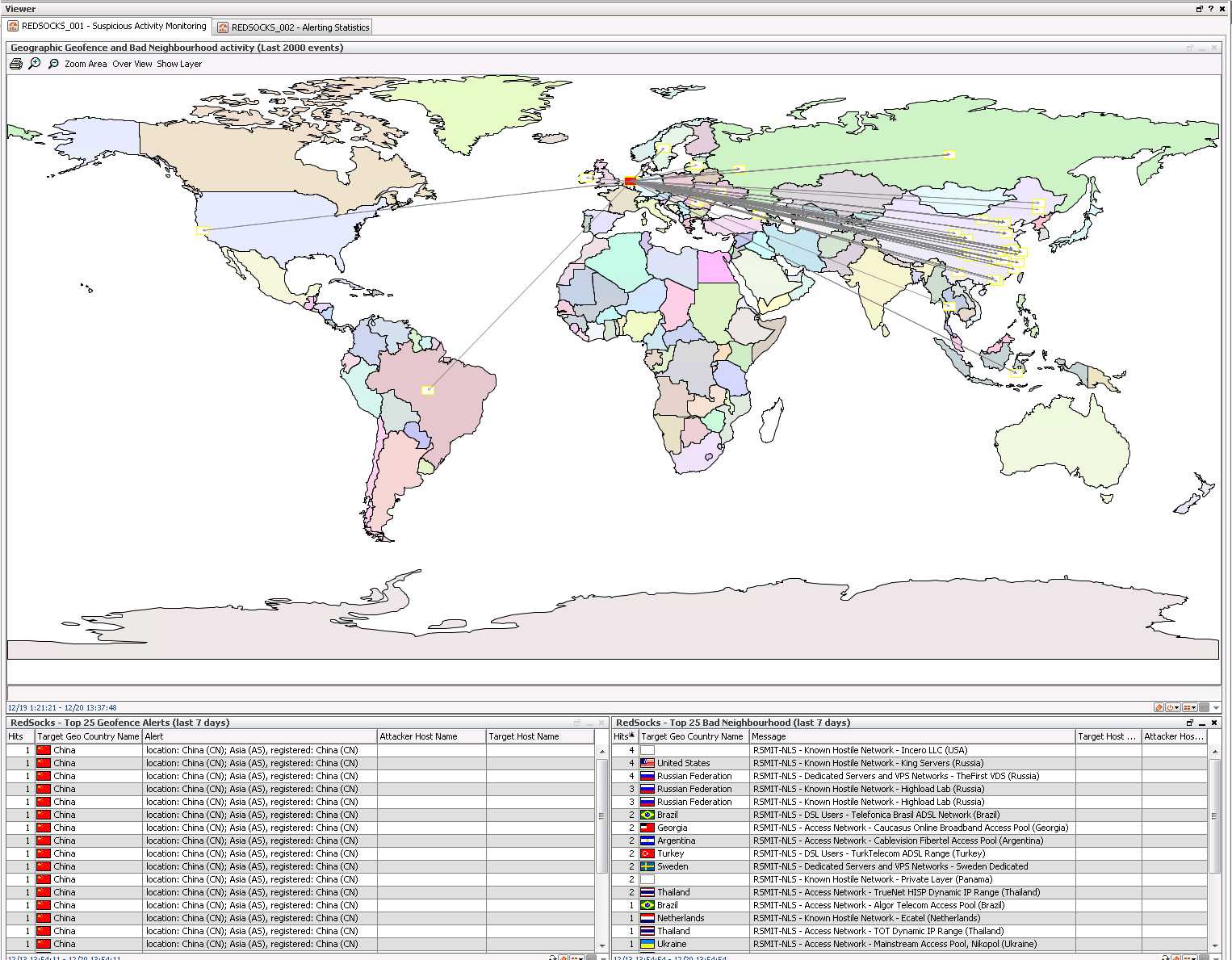
This dashboards shows a Top 25 High Severity Alerts and Top 25 Alerts by Name both shown in a table and as a chart. The main use case for this is to use for monitoring and IDS finetuning.
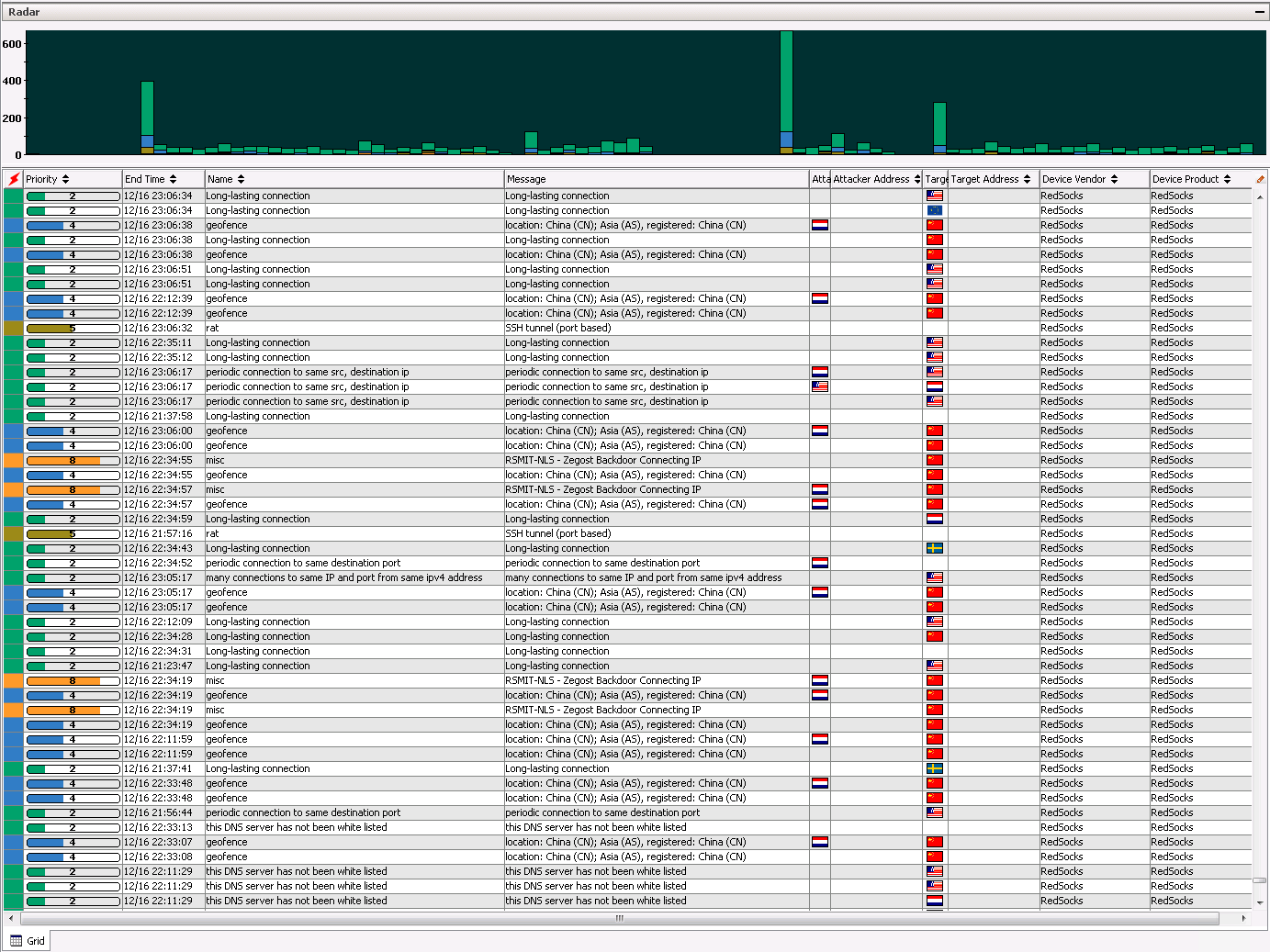
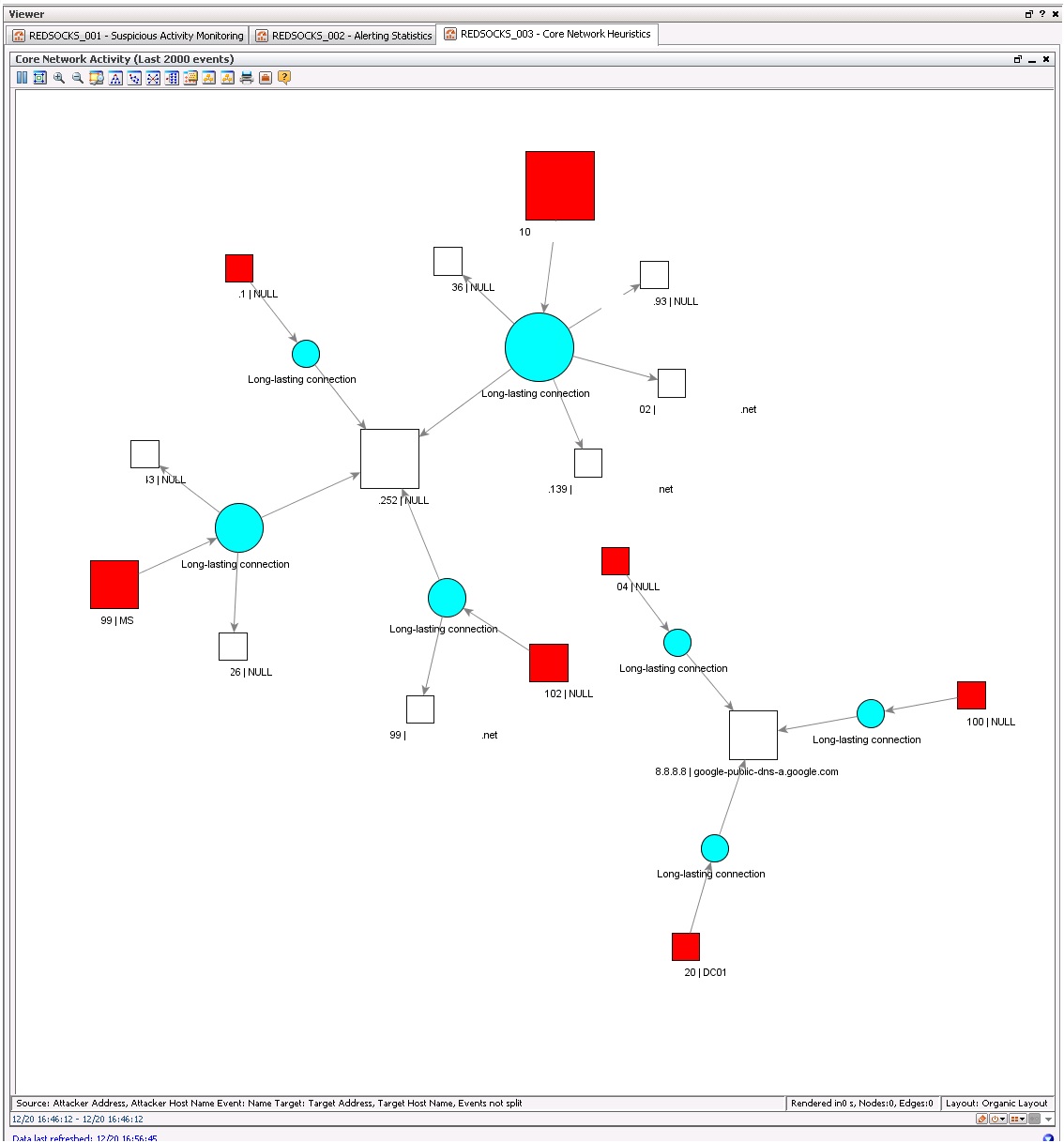
This dashboard shows a Core network model based on network heuristics (making use of the last 100 events). The use case for this is to easily analyse anomaly's in network traffic.
Note: Traffic has been censored
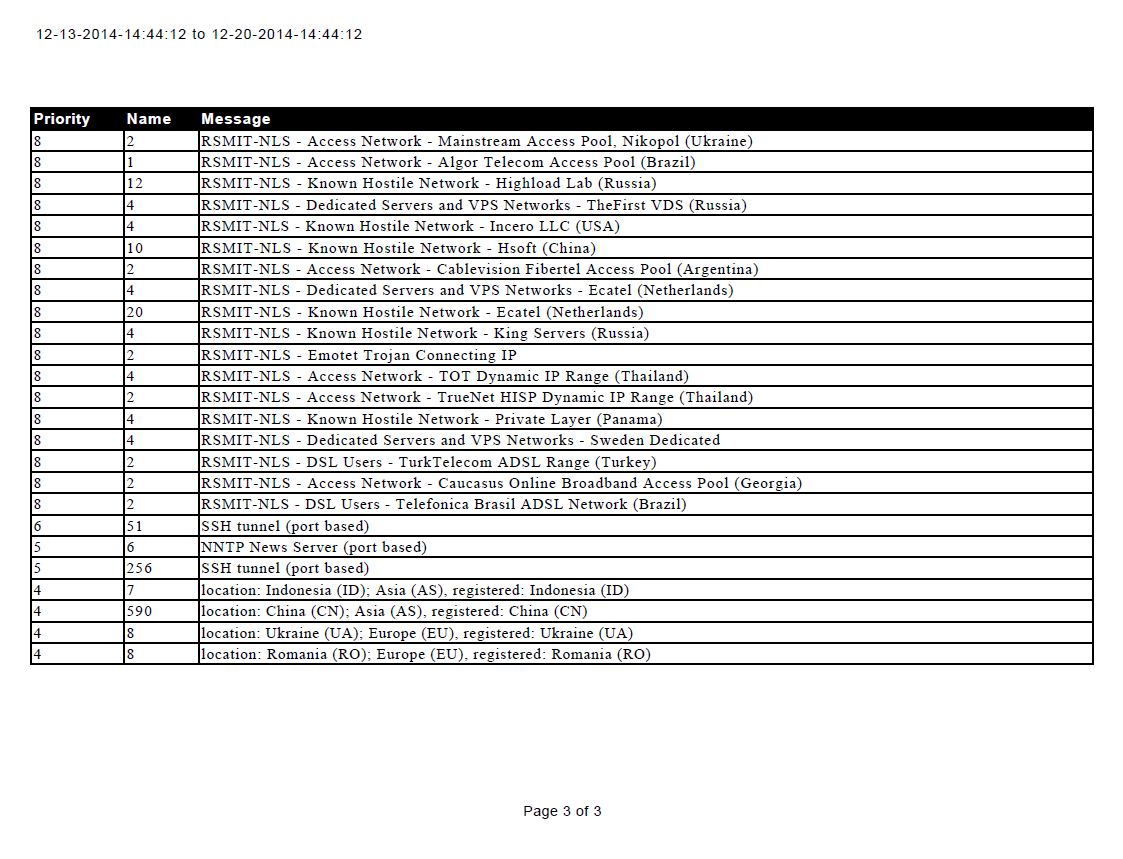
Reports
This report shows Top 25 High Severity Alerts in a PDF report, the use case is useful for auditing/compliance and reporting to possible ISO's/other stakeholders as a KPI/threat landscape indicator.
Conclusion
A SIEM can bring alot of added value to a netflow IDS appliance like RedSocks but it needs to be properly finetuned according to a risk driven approach. If its properly fine tuned you can get the maximum aimed value out of the combo: IDS/SIEM. This was a basic example of possible use cases, but here are some other advanced use cases that can be achieved using Arcsight:
- Add Arcsight's Network Model to give more insight into traffic (from and too VLANS) for Core network model based on network heuristics.
- Correlate RedSocks triggered alerts with Anti-virus virus detections to increase detection certainty.
- Correlate Data Leakage Prevention hits with filesharing activity detected by RedSocks to finetune the DLP solution.
- Correlate Geofence activity with Host IDS anomaly's in order to detect "0day malware".
and many more...