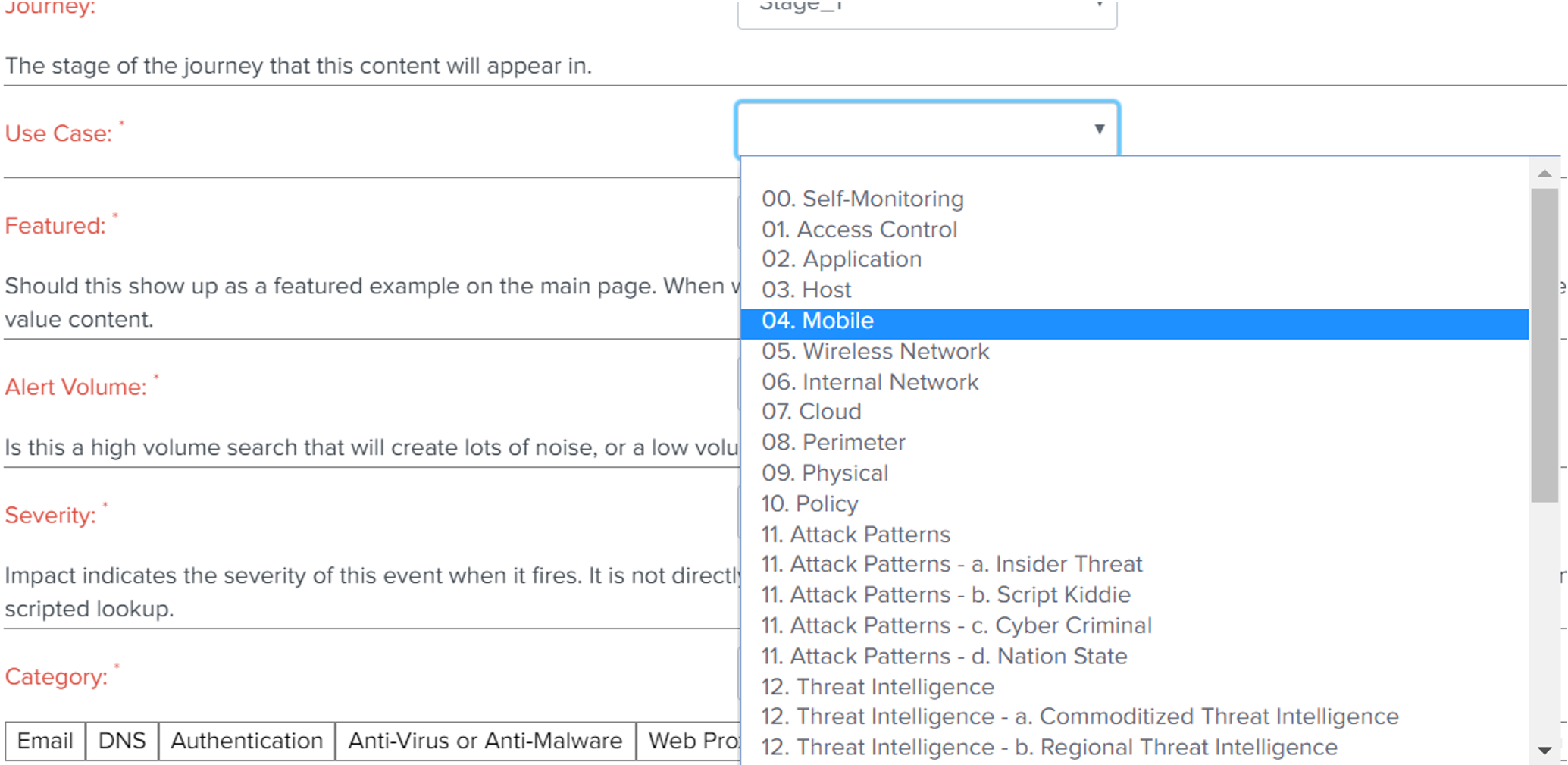
What is a Use Case Framework?
A Use Case Framework is an analytical tool that has a series of cyber security related distinctions which are translated into a directory structure (or categories) that facilitate the organization of cyber security detection rules. The objective of building a Use Case Framework is to better protect the organization’s valuable assets by designing and developing detection use cases using a holistic approach that connects (with always newly emerging) regulatory, compliance and threat requirements. The framework provides more granular control over its detection coverage and ongoing development.
UPDATE: I have updated the framework with Splunk implementation example (v1.1)
Downloads:
SPEED Use Case Framework v1.1.pdf
ArcSight ARB Package.arb (just the rule directories)
QRadar Bundle Package.zip (just the rule directories)
ELK Elastalert Bash Script.sh (just the rule directories)
Note: this is all licensed under Creative Commons Zero license. Do what you want with it.
https://github.com/correlatedsecurity/SPEED-SIEM-Use-Case-Framework
You can connect with me on LinkedIN if you appreciate my work: https://www.linkedin.com/in/jurgenvisser/
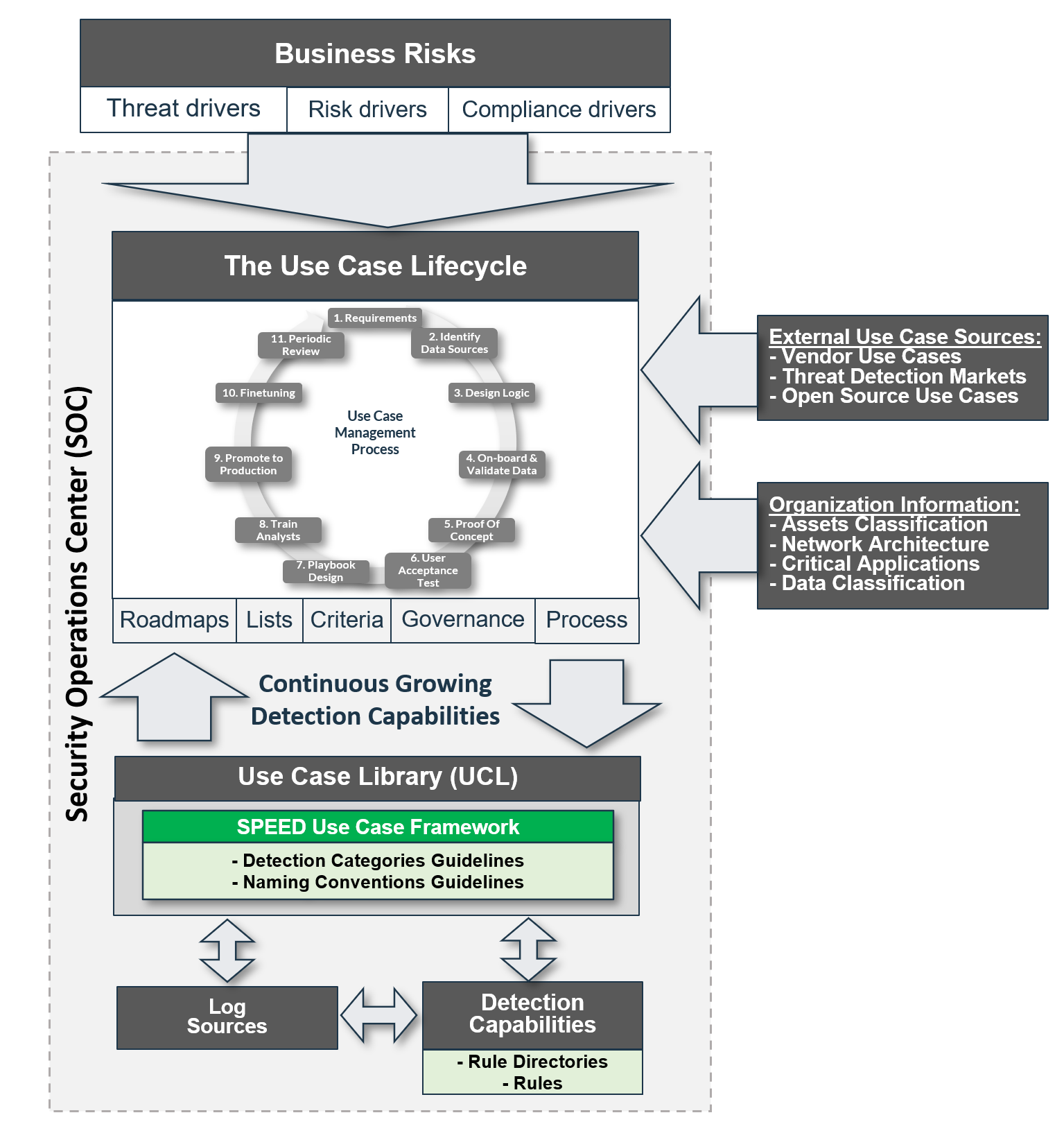
Why a Use Case Framework?
• To have a holistic “frame of reference” where detection use cases can be categorized into.
• To quickly see where your use cases are lacking and need more attention (blind spots).
• To facilitate a phased approach of expanding new use cases based on a large variety of inputs and priorities (Use Case Roadmap).
What are the Key “SPEED Use Case Framework” differentiators?
A. Vendor neutral
B. Separate from the Use Case Lifecycle Management.
C. Agile and Flexible (can be changed later-on)
D. Simple and clear by design.
E. Addresses Qualitative and Quantitative Threat modelling requirements from the Cyber Threat Intelligence (CTI) team.
F. Specific Naming conventions allowing easier integration with SOAR Playbook categorizations.
What is the Added value by the SPEED Use Case Framework?
Clear Location for log source monitoring use cases
Location for generic Threat actor Threat modeling using the kill-chain
Location for threat modeling threat actors like “APT1” using the kill-chain
Key Distinctions between Threat intelligence types
Key Distinction between Attacker-centric and Defense in depth model
Very clearly defined naming conventions that are consistent all over the framework
What Can I do to implement the SPEED Use Case Framework?
1. Start with a Initial SIEM installation (or existing SIEM installation)
2. Disable All Rules (or disable those who you don’t actively use)
3. Structure Rule Directories
4. Determine Implementation Criteria and a Use Case Framework
5. Start implementing and migrating out-of-the-box Use cases to a chosen Use Case Framework with corresponding implementation criteria.
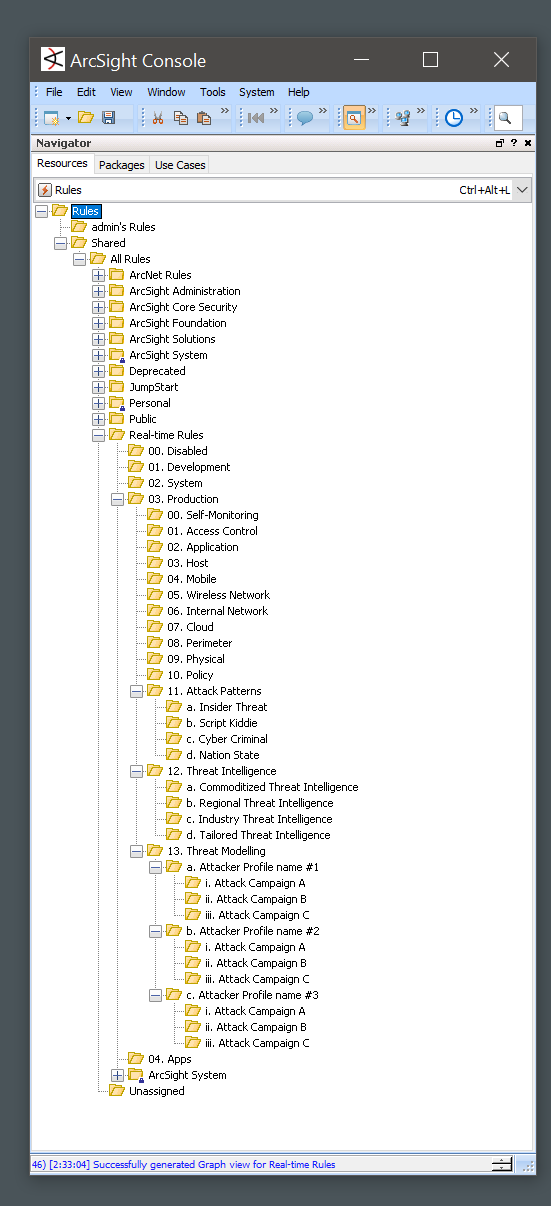
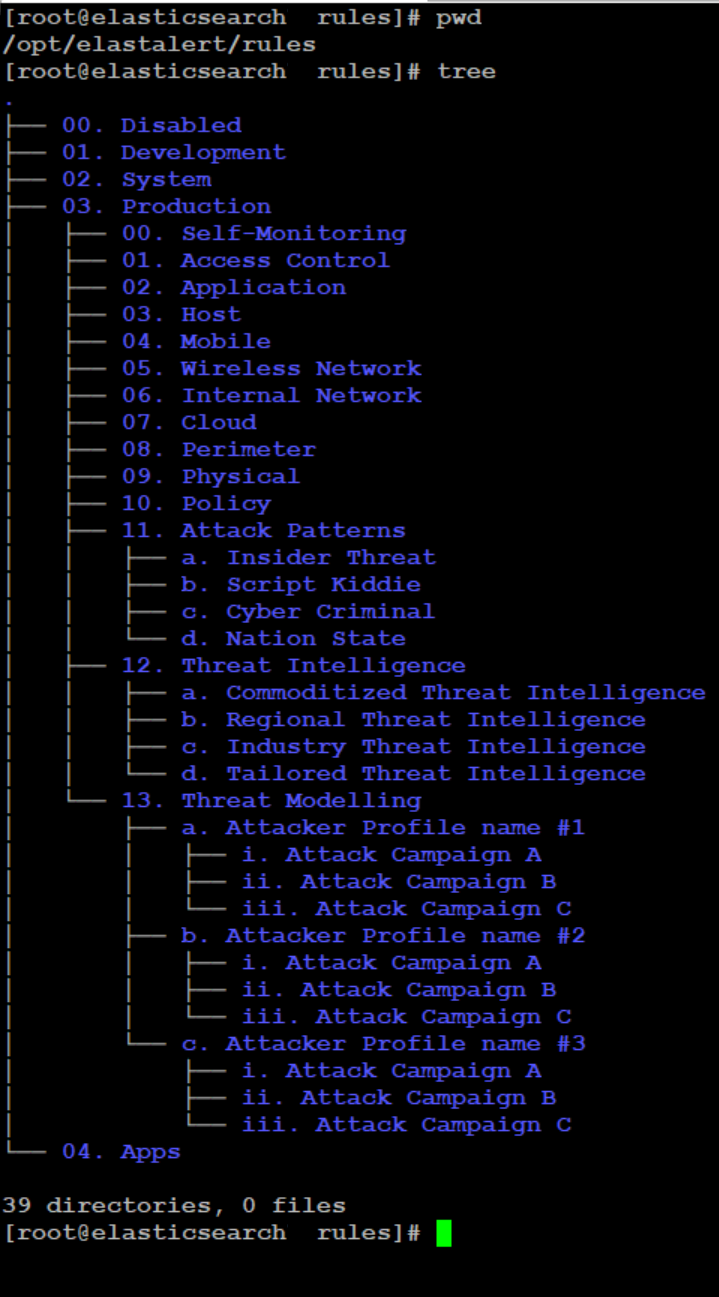
Examples of the directory structure implemented in some popular solutions:
ArcSight ESM
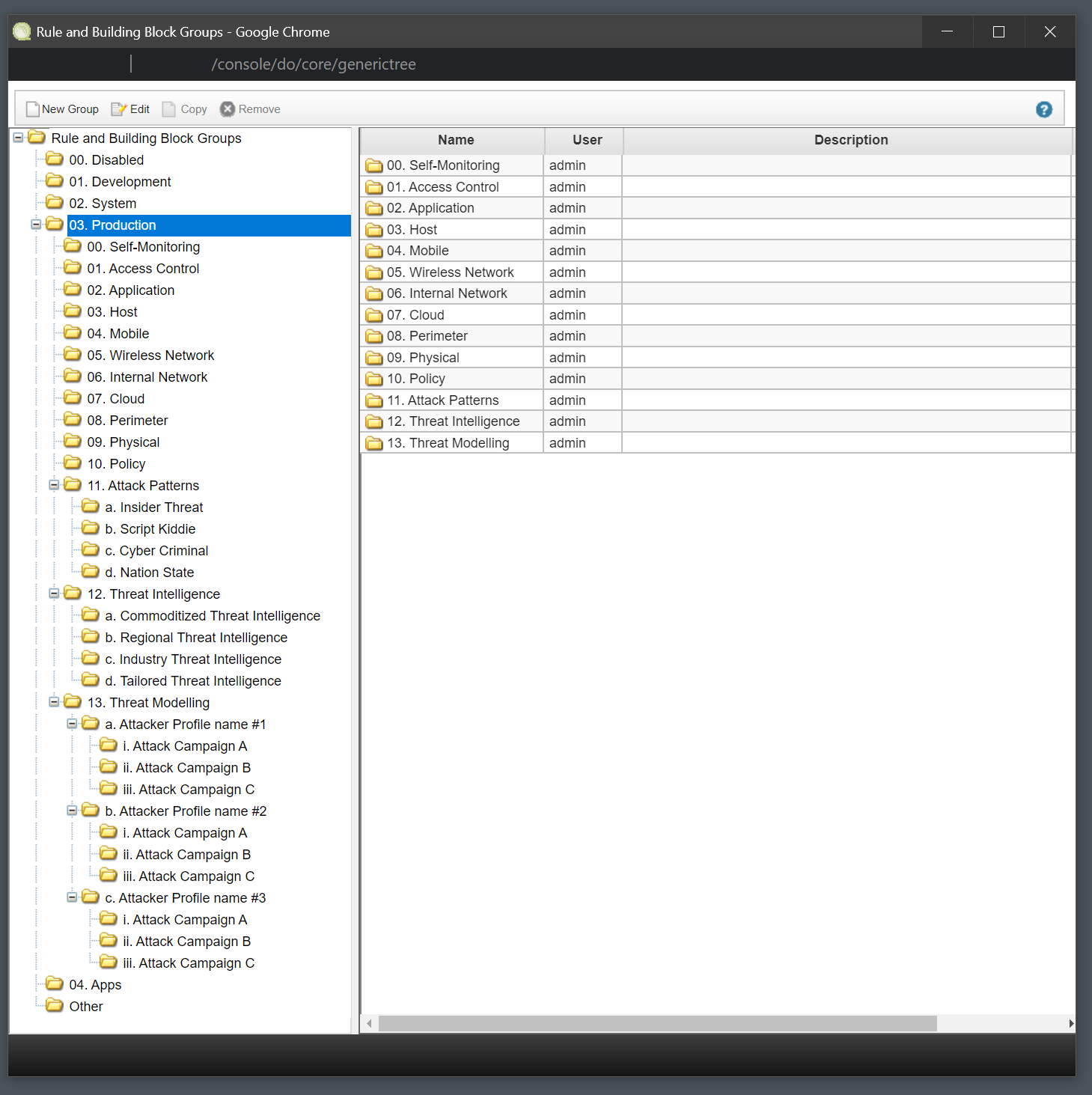
 QRadar SIEM
QRadar SIEM
 ELK Elastalert
ELK Elastalert
 Splunk - Security Essentials App
Splunk - Security Essentials App