Anybody that has been working in (or with) the Cyber Threat Intelligence (CTI) industry has probably come to the conclusion that not all CTI vendors cover the same intelligence sources and sometimes if they cover a source, there are vendors that take a more "quantitative" approach and some vendors that more of a "qualitative" approach.
For example scraping TOR pages and indexing them is a example of a "quantitative" darknet intelligence approach. While actively being on TOR forums and related chat groups is considered a "qualitative" darknet intelligence approach.
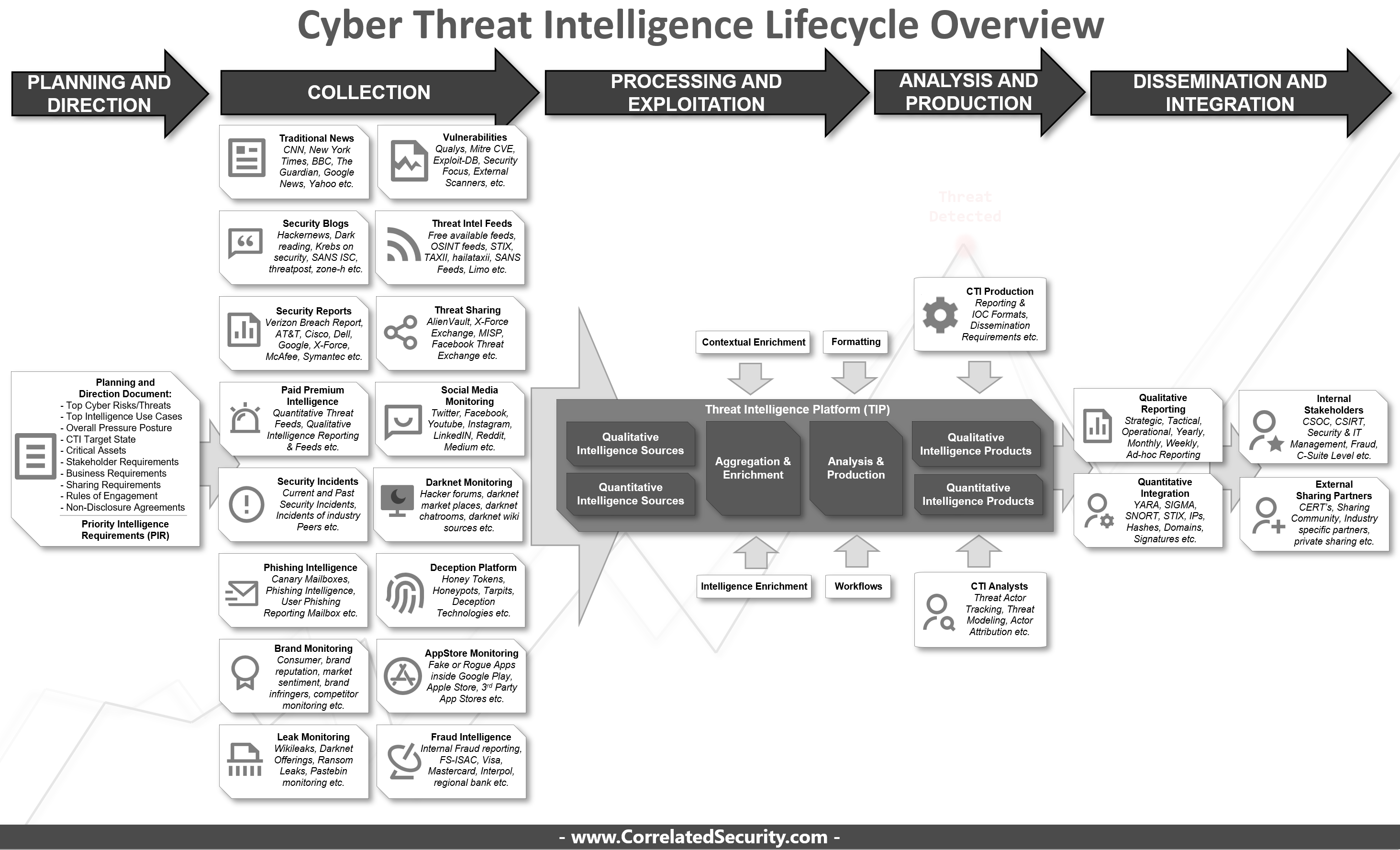
The wide variety of different intelligence sources that are out there is also quite challenging for some to get a handle on when they are just entering in the CTI domain. To help those who are just starting up their CTI program I've created a overview diagram with some key pointers to help them navigate this domain of cyber security.
Critical Note: This diagram is a reflection of the Cyber Threat Intelligence commercial offerings out there and might have not covered all intelligence sources possible in the world.
KEY POINTERS WHEN STARTING YOUR CTI PROGRAM:
1. Start with a "planning and direction document" to derive the Priority Intelligence Requirements (PIR)
2. If you have limited or non-existent budget start with open source/free first.
3. Be aware that a vendor collection scope might overlap but might vary in terms of quantity or quality.
4. There is no one single vendor that does everything perfectly making distinctions between types of vendors helps combining the ideal package based on your PIR's:
- Quantitative Intelligence Vendor
- Qualitative Intelligence Vendor
- Aggregation & Enrichment Platform Vendor
- Analysis & Production Platform Vendor
- Dissemination and Integration Platform Vendor
5. SOAR seems one of the best solutions out there that is able to consolidate, automate and distribute intelligence according to standardized workflows to it's stakeholders (although only a sub-set of SOAR vendors support TIP-like platform capabilities).