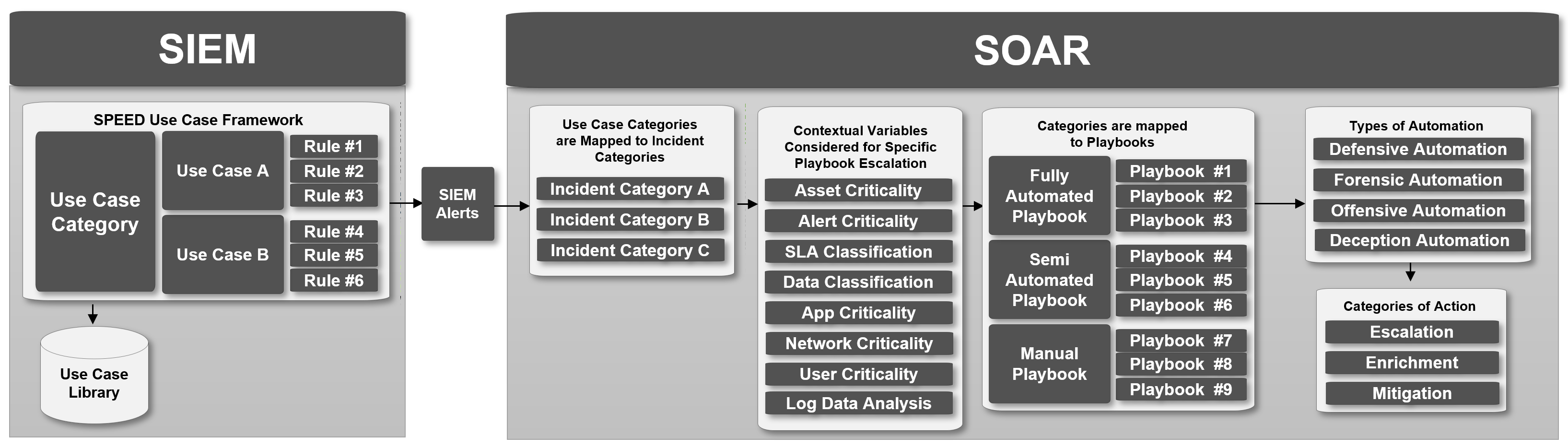
With the emergence of SOAR technologies within the Security Operations domain it is clear that this technology has provided great value to departments swamped with tons of alerts that need to be analyzed (the so-called alert fatigue).
Unfortunately buying a SOAR technology will not simply tackle the problem of alert fatigue directly out of the box. To be able to connect an alert to an automated playbook there needs to be a case by case review of use cases within the SIEM before it can be efficiently and effectively connected with a playbook (this requires a mature Use Case Lifecycle Management and Use Case Framework). For optimal automation there are also several other contextual variables that need to be considered before choosing the right escalation playbook that rely on an existing mature IT organization.
The key SOAR distinctions that users should be aware of before venturing into a SOAR project:
1. SIEM Use Case Categories, Use Cases or SIEM Rules are mapped to incident categories and these categories are then mapped to playbooks.
2. Three types of playbooks
a. Manual playbooks (a series of manual tasks)
b. Semi-Automated playbooks (a hybrid of automated and manual subtasks)
c. Fully-Automated playbooks (completely automated)
3. Four types of Automation
a. Defensive Automation (anything that tries to prevent the threat or risk)
b. Forensic Automation (anything that tries to retrieve additional evidence)
c. Offensive Automation (anything pro-active that tries to investigate an asset)
d. Deception Automation (anything that retrieves or adjusts deception tools)
4. Three different categories of action
a. Enrichment (adding additional CMDB, CTI or environment data)
b. Escalation (e-mail, ticket escalation, chatops communication)
c. Mitigation (the changing of configuration on devices)
These distinctions I have captured in relation to SIEM in the following Diagram.
This provides the SIEM-SOC Automation architecture where we can derive requirements for the deployment of a SOAR solution. These critical success factors and requirements are:
1. Successful automation architecture requires good foundational IT organization
a. Updated and accurate CMDB
b. Network hierarchy and their criticality
c. Data Classification
d. App Criticality
e. User Criticality
f. SLA Ticket Classifications
g. Top Critical Applications List
h. Clear Security Incident Ticket Categories
i. Security Incident Management process
2. Key automation success lies in SIEM integration, Use case Lifecycle Management and Use Case Framework
a. A SOAR solution that can integrate very intimately with your SIEM solution
i. Pull additional correlated logs from an alert from the SIEM
ii. Map every field from the alert to a SOAR case field
iii. Ability to map SIEM severity levels to SOAR severity levels
iv. SIEM Alert Timestamps become extremely important when escalating and measuring SLA performance on a SOAR solution make sure these are also left in-tact.
b. A Mature Use Case Lifecycle Management process
i. Allows for Additional “automation integrations Priority List” next to the Use Case and log source onboarding priority list.
c. A Use Case Framework with a clear structure
i. Having naming conventions that allow mapping of use case category level, Use Case level or Rule specific level playbooks
ii. Having a clear categories of use cases to group entire categories to playbooks for efficient and effective automation.
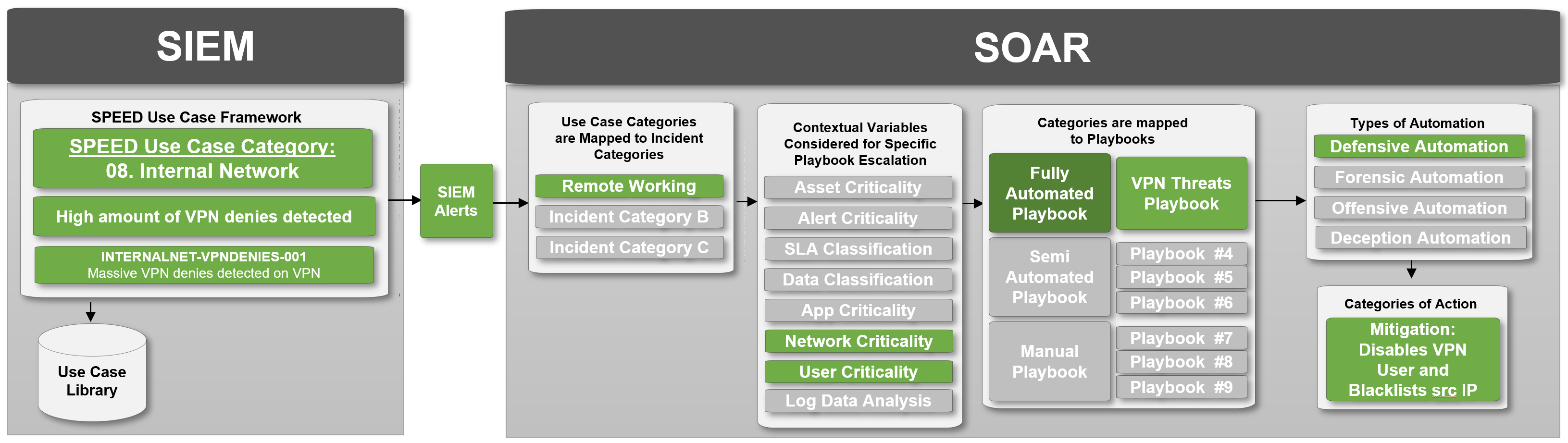
In the following example a use case category and naming convention of the SPEED Use Case Framework is mapped against an example use case flow from SIEM to SOAR providing insight into the inter-dependencies of both systems.
Conclusion
Implementing a SOAR solution relies on a series of matured services within the existing IT organization and the Success of a SOAR automation project will highly depend on these maturity levels. Specifically, for the SIEM where Integration, Use Case Lifecycle Management and Use Case Framework need to be fully matured before venturing into a SOAR solution.
It is generally very hard to find an organization to have all proposed requirements of these fully matured inside their IT organization and on top of that, being able to do an automated API call and get all the information needed for an automated playbook.
This in turn gives rise to the new generation cloud-native SIEM and SOAR solutions that are based inside the API-centric cloud architecture and easily can enrich, escalate and mitigate any security issues within its environment.
This conclusion provides insight into the future of A.I. for Cyber security (machine learning, Machine Understanding and Machine Action) within an IT infrastructure. This will be the organic evolutionary growth path of SIEM and SOAR co-existence within the Security Operations context.
With this article I've tried to provide insight into why SOAR Success heavily depends on key existing foundations within the IT organization and critical SIEM dependency. If you liked what you've read you can always connect with me on Linkedin: