Security Analytics for Data Driven Risk Decisions
Security Analytics is an overused buzz word in the security industry. But, What is it? What can you do with it? and Who can use it? I will try to answer these questions in this post.
What is Analytics?
Analytics is the discovery and communication of meaningful patterns in data.
What is Security Analytics?
Security analytics refers to information technology (IT) solutions that gather and analyze security events to Communicate insight and enable IT staff to analyze and Discover events that pose the greatest risk. Solutions in this area include, but are not limited to Security information and event management (SIEM) solutions and user behavior analytics (UBA) solutions.
Why Security Analytics?
Security Analytics is mostly used when someone is trying to analyze security events from log data or from report data in order to Communicate insight inside their infrastructure or Discover New Anomaly's (potential risks) inside their environment.
These two things solve two existing problems which some Security Operation Centers (SOC's) or Incident Response (IR) teams have.
1. Problem: Most SIEM/IDS/IPS Reports are static and do not allow for easy drill-downs
Solution: Communicate insight through tools that allow easy filtering and visualizing.
Most PDF reports out of SIEM/IDS/IPS systems are just statistics or charts which cannot be filtered or modified to drill-down to more specific data (mostly these are just top 10's). This can be unpractical for some Security Analytics that want to get some Cyber situational awareness in their environment. By using exported data to a .CSV file this can be analyzed in depth and filtered to allow better drill-downs.
2. Problem: SIEM/IDS/IPS visibility of the network limited
Solution: Discovery New Anomaly's through extensive data-set visualization, data mining and query'in.
Existing intrusion detection/prevent systems (IDS/IPS) or Security Information and Event Management (SIEM) systems only see what they are programmed to see as abnormal (rules). To discover what else is going and to build new use cases out of this a select amount of data can be used to visualize and discover new patterns in.
In the survey, 37% of respondents said that their teams are unable to distinguish malicious events from nonevents, and 45% cited lack of visibility into events across a variety of systems and domains as key impediments to effective IR. Together, these answers suggest the need for more precise conditions for security information and event management (SIEM) alerts, as well as the need for more specialized IR skills. - Source: SANS 2015 incident response survey
Data-informed Decision-making
By solving these two issues with security analytics it will allow the organization(s) to be able to practice Data-informed decision-making (DIDM). This refers to the collection and analysis of data to guide decisions that improve the quality of organizational processes, strategic decisions and deciding on risk treatment in a more effective way.
Security Monitoring vs. Security Analytics
Some people confuse Security Analytics with Security Monitoring. The following table can help clear things up in two big camps: Alert-driven vs. Exploration-driven.
| Alert-driven (Security Monitoring) | Exploration-driven (Security Analytics) |
| SIEM | (Big Data) Log Management |
| Incident Detection | Incident Discovery |
| Reactive | Proactive |
| Like Tech Support | Like Q&A |
| Reaction | “Hunting” |
| Alert-centric | Question-centric |
| Explore alert context | Explore full context |
| Drill-down | Drill multiple ways |
| Triage/Analyse THIS entity | Explore THIS direction |
| Want to be done with the alert | Want to know whats really going on |
| Operations - Alert Volume | Research - insight usefulness |
Analytics Maturity Model
Security analytics has the primary focus in explaining the following two questions of the Analytics Maturity Model:
- What happened? (Descriptive Analytics)
- Why did it happen? (Diagnostic Analytics)
Predictive and prescriptive analytics are mostly not the ambitions of most security analytics solutions but the ideal situation is that someone will receive receive a text with a predicted data breach in X amount of time with the suggested countermeasures to mitigate or eliminate this risk.
The following maturity model shows the path to the golden goose: a "data-driven" security program.

Presuppositions
- If it isn't beautiful, it isn't true (yes some people unfortunately hold this believe).
- A visualization is worth a 1000 log lines (The fastest way you get information into someone's brain, is through visualization).
- A security analyst is someone whose input is evidence and whose output is True Positive, False Positive, True Negative or False Negative
How to do Security Analytics?
These are the most common situations where security analytics can be applied.
- A security analyst has a triggered security alert and wants to further investigate.
- A security officer receives a security report with statistics around security alerts.
- A "hunter" security analyst want to discover potential bad actors in the environment.
In order to be able to ask questions, proactively explore the full context by drilling down in multiple ways in the data. Most people export their data to a .CSV file with a limited set of columns. This is entirely dependent on the initial question you have regarding the potential risk and which data you need to potentially discover and communicate insight to your question. So the person can eventually communicate and discover insight into potential security risks in the data.
Most people believe in the big data concept of "unstructered data" and being able to do analytics over this. This is not possible, you need some sort of categorization over your data in order to find patterns in it in a visual way.
Once you have the CSV file or an example CSV file, sources found here:
1. http://datadrivensecurity.info/blog/pages/dds-dataset-collection.html
2. http://mirror.simwood.com/honeypot/
3. https://visitrend.com/ has some examples inside their product
There are also multiple ways to export data from systems you may have in your enterprise: SIEM, Firewall, IDS/IPS, E-mail security appliances, proxy servers etc.
Tools
Once you have a question and a dataset you can put it in a tool to start visualizing, here are a couple of tools presented.
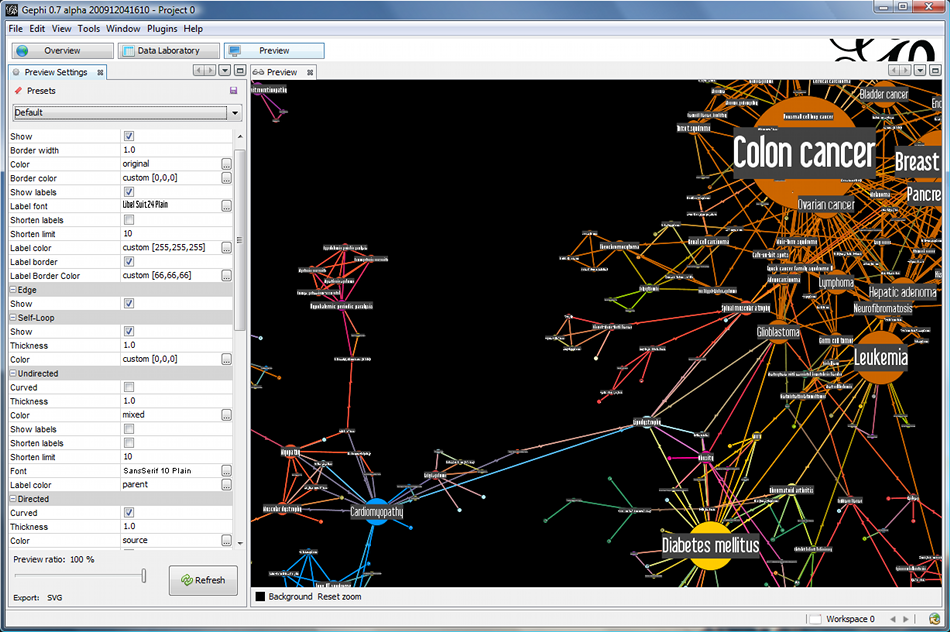
1. Gephi
Gephi is an open-source network analysis and visualization software package written in Java on the NetBeans platform, initially developed by students of the University of Technology of Compiègne (UTC) in France. - http://gephi.github.io/
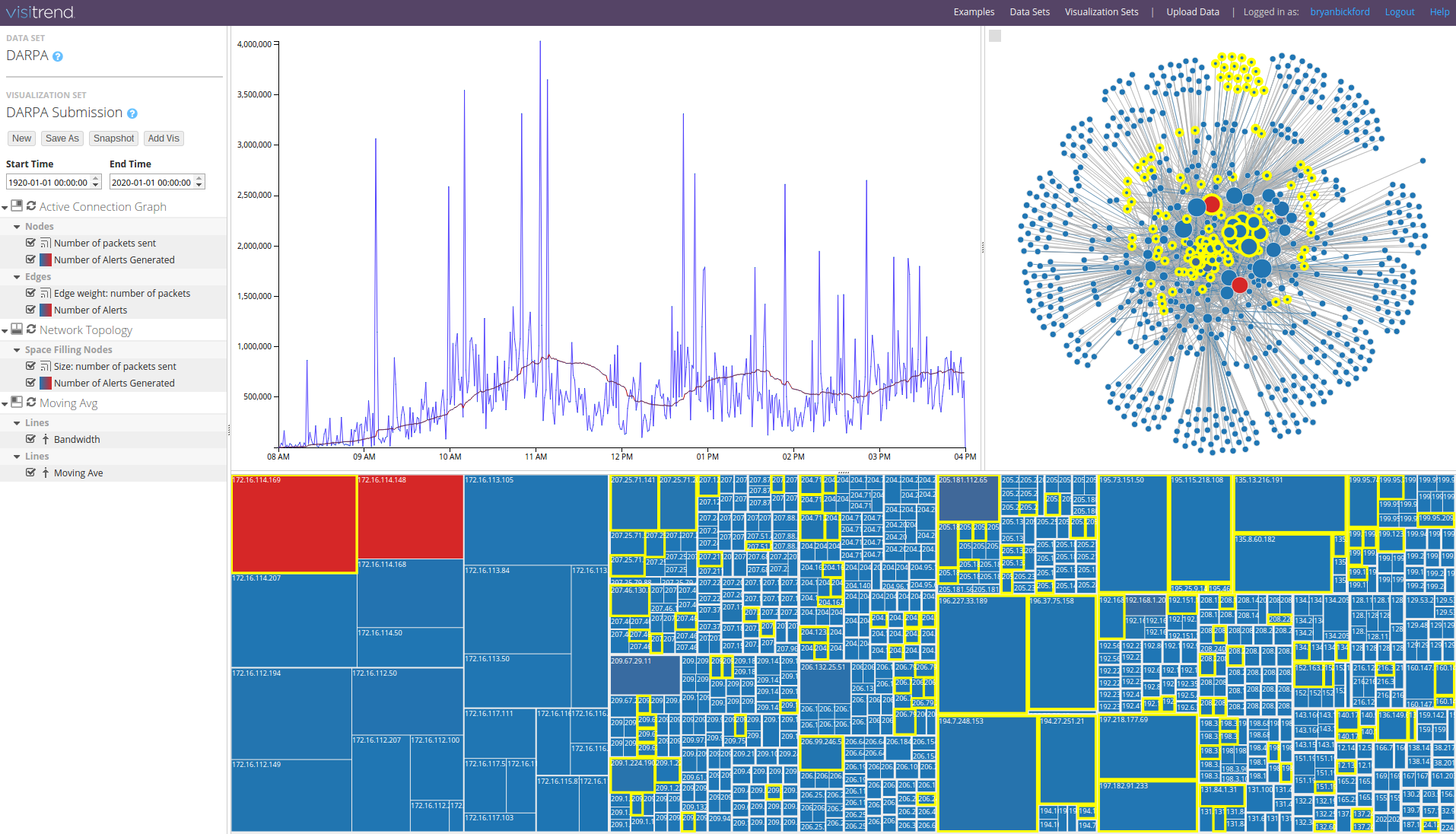
2. Visitrend
VisiTrend is an online platform for big data and cyber security analytics, available as a SaaS service or in appliance form. - https://www.visitrend.com/
3. Tableau
Tableau is business intelligence software that allows anyone to connect to data, then visualize and create interactive, sharable dashboards. - https://www.tableau.com/

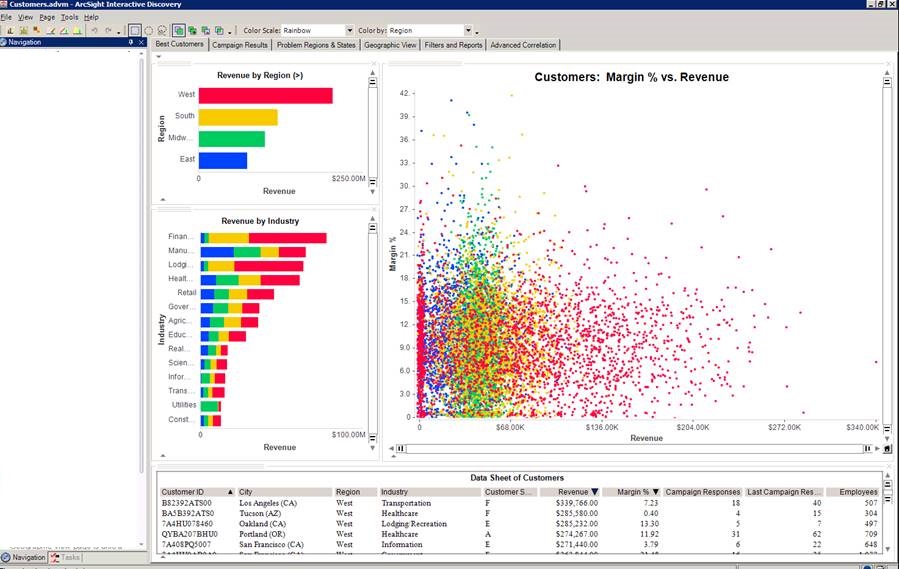
4. ArcSight Interactive Discovery
ArcSight Interactive Discovery visualization software helps IT security professionals instantly pan, zoom and switch perspectives across complex technical data to perform in-depth analysis of security data and discover risks they might have otherwise missed. Interactive Discovery includes out-of-the box, pre-defined and customizable visual perspectives designed specifically for security data analysis out of HP ArcSight SIEM Solutions. - http://www8.hp.com/us/en/software-solutions/enterprise-security.html
At the end of every analytics activity is a rule
After you answered your question through the following formula: QUESTION + DATASET (CSV) + ANALYTICS TOOL. There is a possibility you found some kind of pattern in the data that indicates malicious activity. You probably have taken action on it to mitigate or eliminate this risk. But how will it be detected next time? again by exporting a CSV and doing analytics by hand? too much hassle.
At the end of every analytics activity there should be a rule created to automatically detect these patterns in the future. So the outcome should be a Use Case for your IDS/IPS/SIEM or Analytics solution of choice. There are solutions trying to attempt to tackle this issue in a combined solution (look at User Behavior Analytics solutions) although these are currently mostly focused on insider threat.
Conclusion
All in all security analytics will get more popular the more people see security event data as a valuable asset to guide risk decisions inside the organizations. But it is still at the moment in it's early stages of development.