What's Your Approach to Building SIEM Use Cases?
Goal/Why?
This article will describe models and processes to deal with two existing components of the SIEM Use case problem.
- Prevent organizations from building ineffective uses cases with low value in their SIEM.
- (trying to) Answer or solve the philosophical question: "Which SIEM use cases has most value/effect for the organization?"
To make it all work in a pragmatic and effective way, the goal is to create two end products.
1. Create a "SIEM Use Case Roadmap".
2. Periodicly prioritize and review the "SIEM Use Case Roadmap" based on the following two points:
A. An approach which directs the organization on the "right" SIEM use cases road.
B. Input from different stakeholders and the chosen approach.
Presuppositions
Here are a few presuppositions which this article is based on
- A Successful SIEM implementation requires clear priorities determined by a risk-based approach/strategy.
- The 80/20 principle (20% of SIEM use cases are responsible for eliminating/mitigating 80% of the risks).
- A good use case enables to respond quickly to business impacting security alerts.
- In order to have an effective set of SIEM use cases an appropriate method must be applied.
- SIEM use case development is an agile process which is able to adapt in response to a changing threat landscape.
- The strategy: LOG EVERYTHING and AUDIT EVERYTHING (in case of a SIEM) is ineffective and has low value.
Risk Approach/Strategy
When deciding on a Risk Approach/strategy it's useful to have input from the Board of Directors through the following question:
- What are the top three security priorities/risks in our organization?
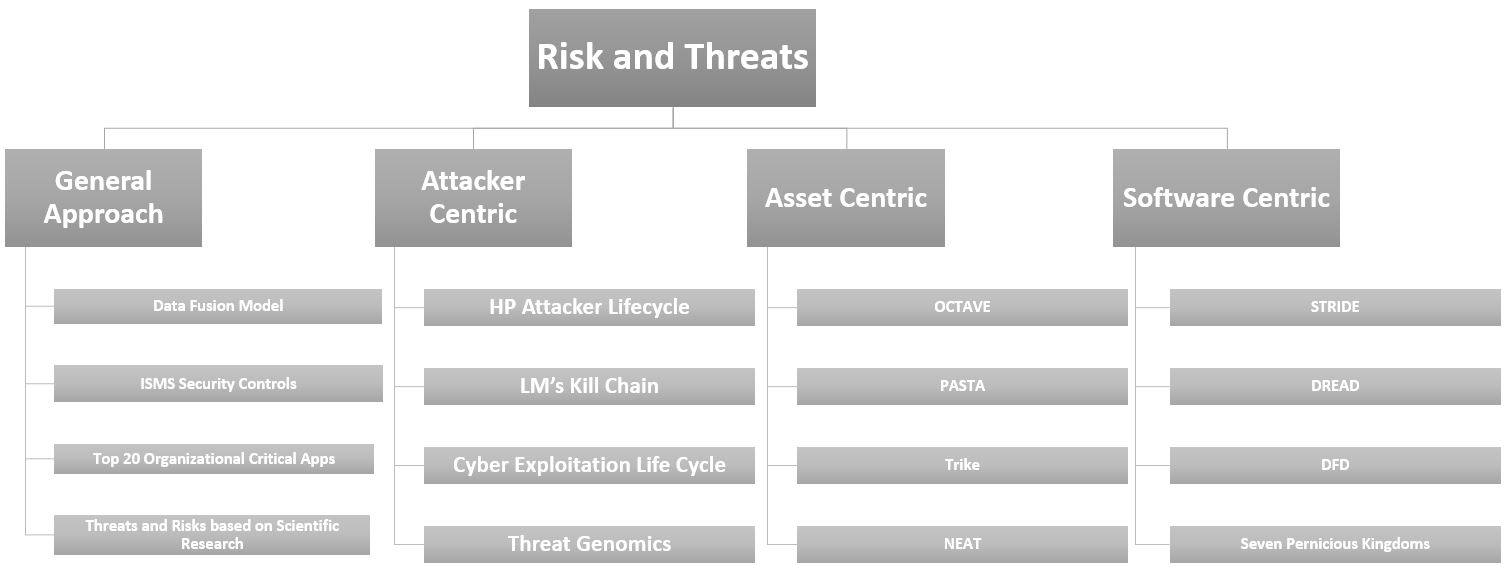
These are the three models used in threat modeling and one general one to put the other models i've found in.
- General Approach A holistic approach to risk and threats.
- Attacker-centric Anticipating modes and targets of attack and preparing defenses.
- Asset-centric Determining value within the network and protecting what matters most.
- Software-centric Stopping vulnerabilities before they can become threats.
Based partly on HP Protect 2014 presentation: BB3173 - Threat modeling Kill chains, diamond models, and the 50-yard line - Angela Gunn
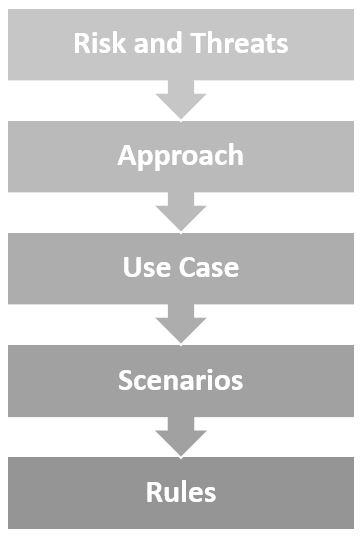
Use Case Meta Levels
Use cases should be risk-driven, this model gives insight into the relation between use case concepts used in this article.
Use Case building methods
These are tactical model to determine your use case roadmap.
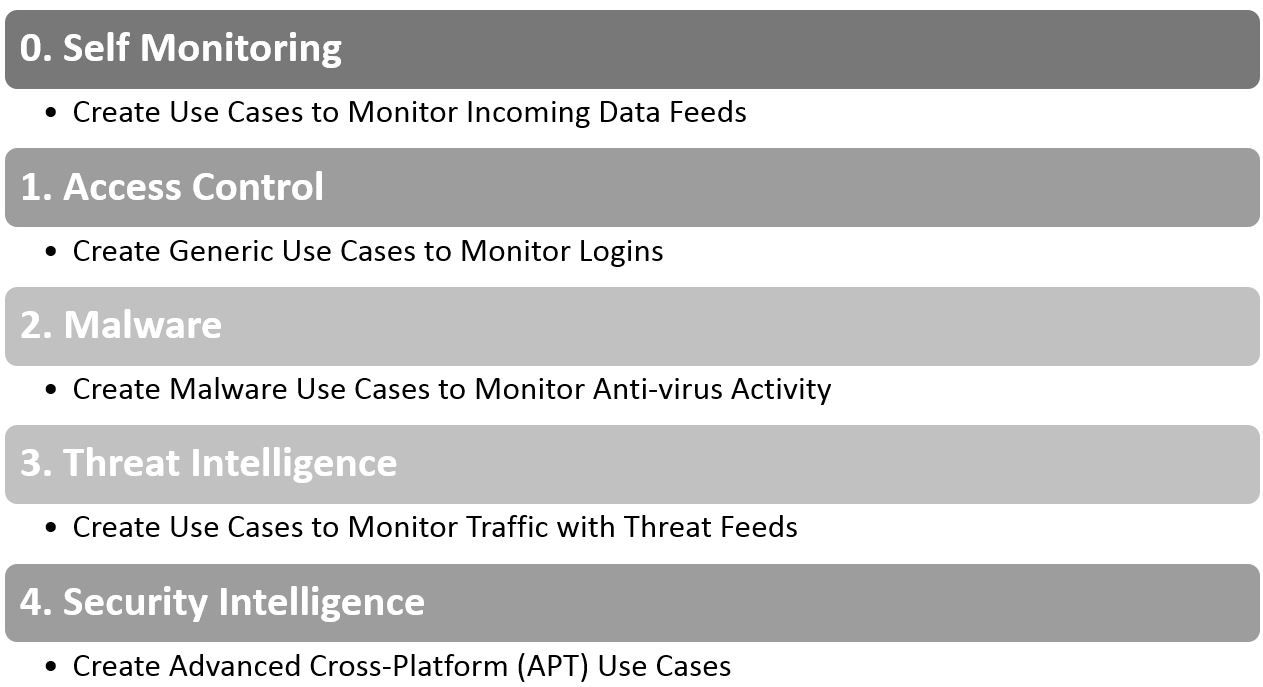
Use case priority per general domain
This is a generic model used by most practical SIEM specialists to start doing use cases.
HP Activate Framework - Data fusion model
The HP Activate Framework has two parts: the Data fusion model and the HP Attacker Lifecycle. It starts with the data fusion model to build the foundation and continues on to the HP Attacker lifecycle for more advanced use cases.
See HP Protect 2014 presentation: TB3267 - ArcSight Activate Framework - Petropoulos

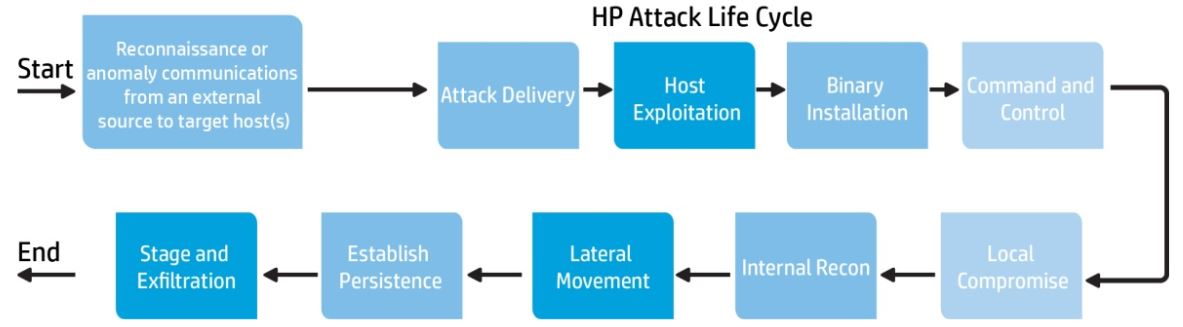
HP Activate Framework - Attacker lifecycle
This model can be used stand-alone or together with the activate framework. See HP Protect 2014 presentation: TB3267 - ArcSight Activate Framework - Petropoulos
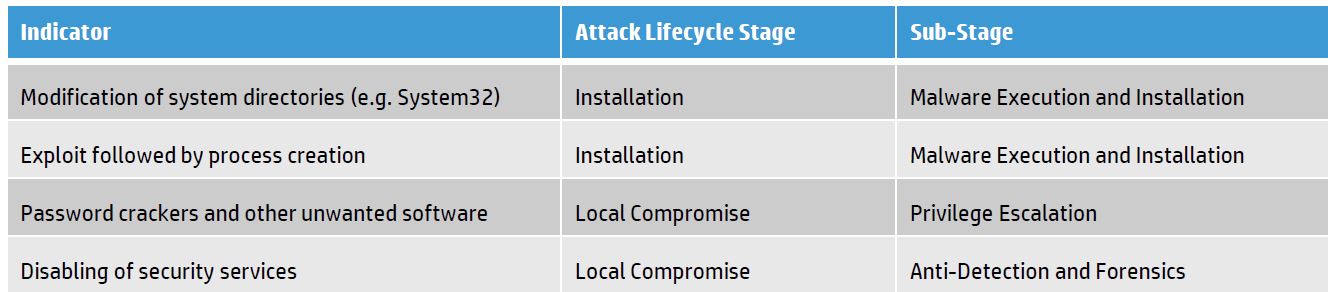
The HP Attacker Lifecycle (based on Lockheed martin's kill chain) Methodology for building use cases is found here:
http://www8.hp.com/h20195/v2/GetDocument.aspx?docname=4AA4-9490ENW
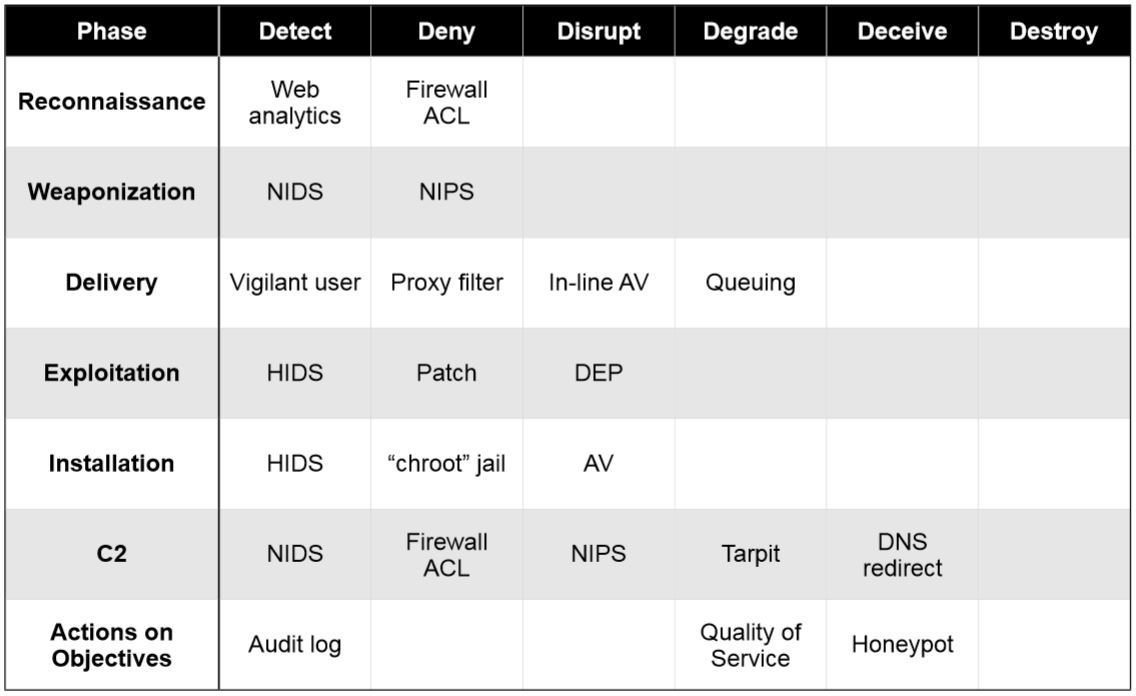
Lockheed Martin Kill chain
The Lockheed Martin's kill chain as an example is mostly used to
Lockheed Martin's Intel Driven Defense using the Kill chain model whitepaper is found here:
http://www.lockheedmartin.com/content/dam/lockheed/data/corporate/documents/LM-White-Paper-Intel-Driven-Defense.pdf
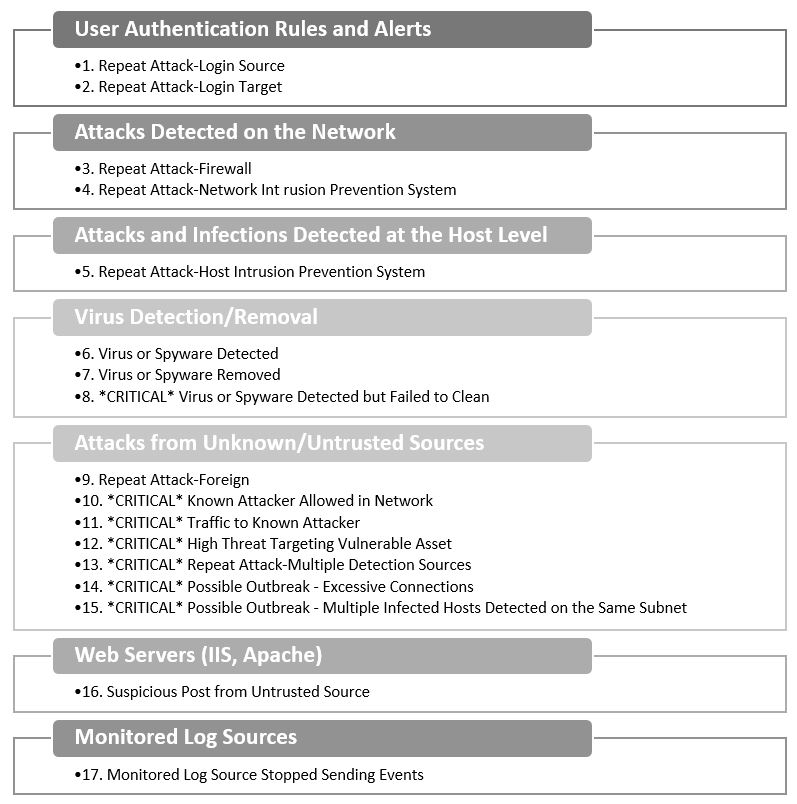
SANS Use Case Strategies
SANS published a whitepaper describing successful SIEM Log management strategies for auditing and and compliance.
The SANS whitepaper is found here:
http://www.sans.org/reading-room/whitepapers/auditing/successful-siem-log-management-strategies-audit-compliance-33528
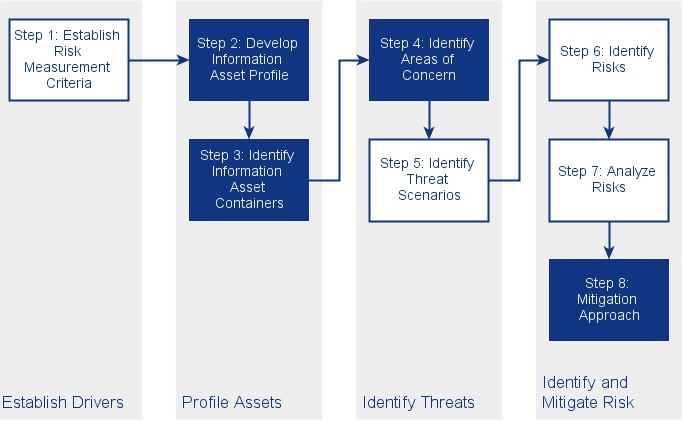
OCTAVE risk assessment to determine use cases
Operationally Critical Threat, Asset, and Vulnerability Evaluation (OCTAVE) Allegro methodology, its approach and terminology. OCTAVE Allegro is an asset centric and lean risk assessment successor of the OCTAVE method.
http://blog.csnc.ch/2013/04/lean-risk-assessment-based-on-octave-allegro/
There are many other approaches named in risk strategy model, I guess it's all relative which one is better.
Data Feed Roadmaps
It's a misconception to just connect EVERYTHING and log EVERYTHING to your SIEM. This is appropriate for a big data log management solution but not for a SIEM. A SIEM is use case-driven not input-driven. Data Feeds should be prioritized by the following two criteria:
- Amount of added value.
- Is it helpful to the Operation?
- Are there any uses cases for this log source?
- Effort to collect them.
- Does it need a customer parser?
- Does the log source need a lot of maintenance?
Data feed roadmap
Here is a general data feed roadmap for your SIEM and log management environment. Based on the following HP Protect 2014 presentation:
TT3052 - HP ArcSight Data makes the difference - Mitchell Webb John Rouffas
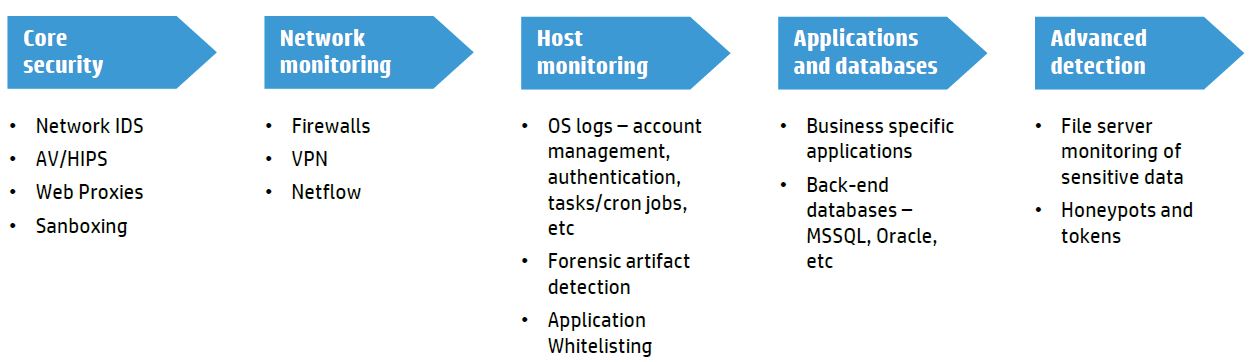
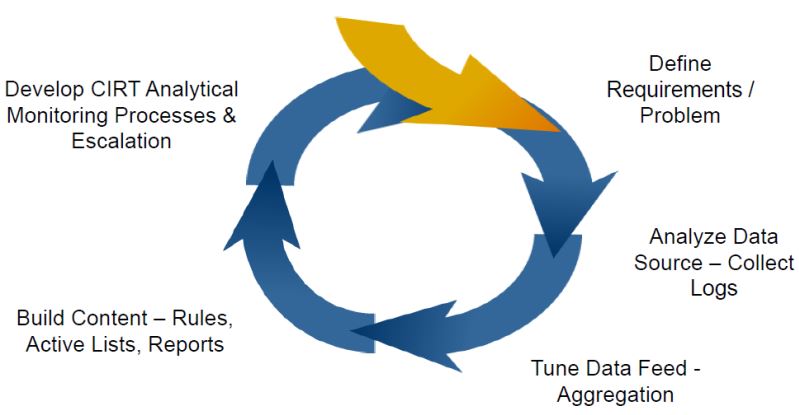
Data feed audit policy determination
To determine your data feed audit policy you can map existing event categories to the HP Attacker lifecycle model.
Data feed lifecycle model
To determine your data feed audit policy you can map existing event categories to the HP Attacker lifecycle model.
Use Case Processes
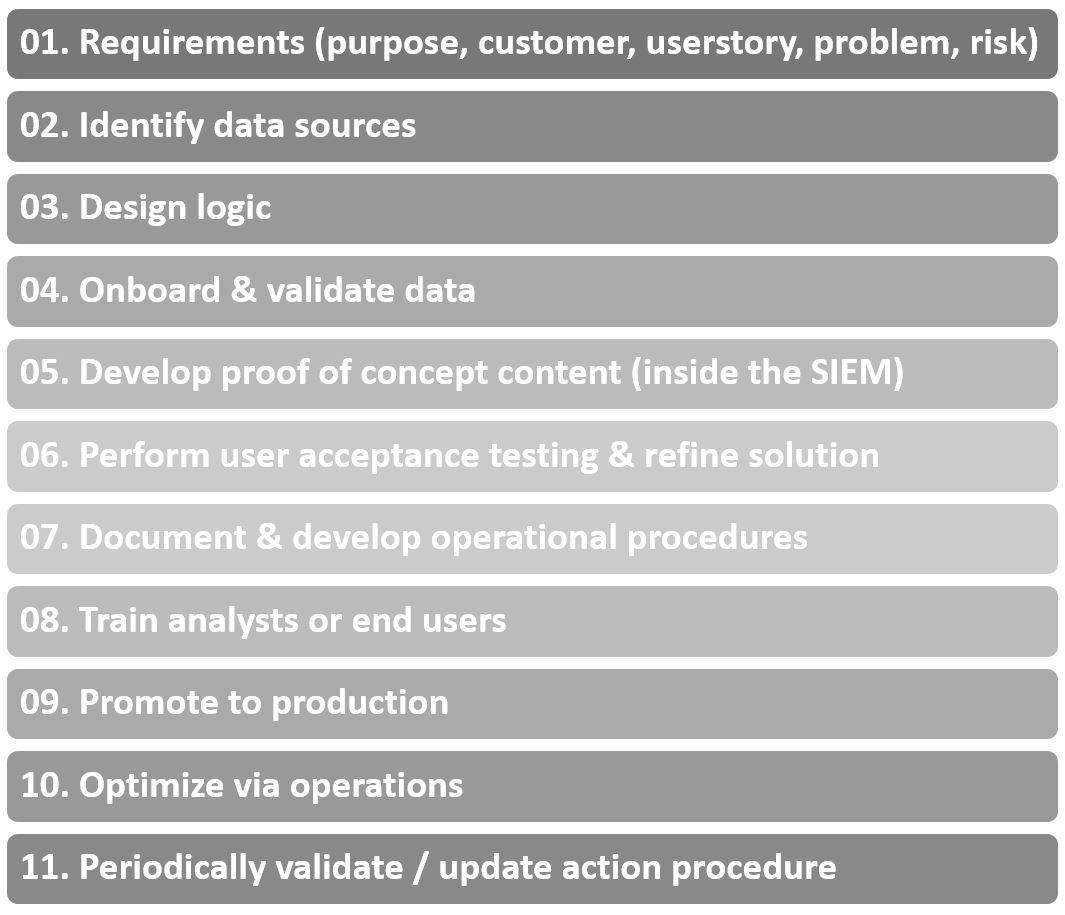
Use Case Building Process
This is a common use case building model for building use cases on a process level.
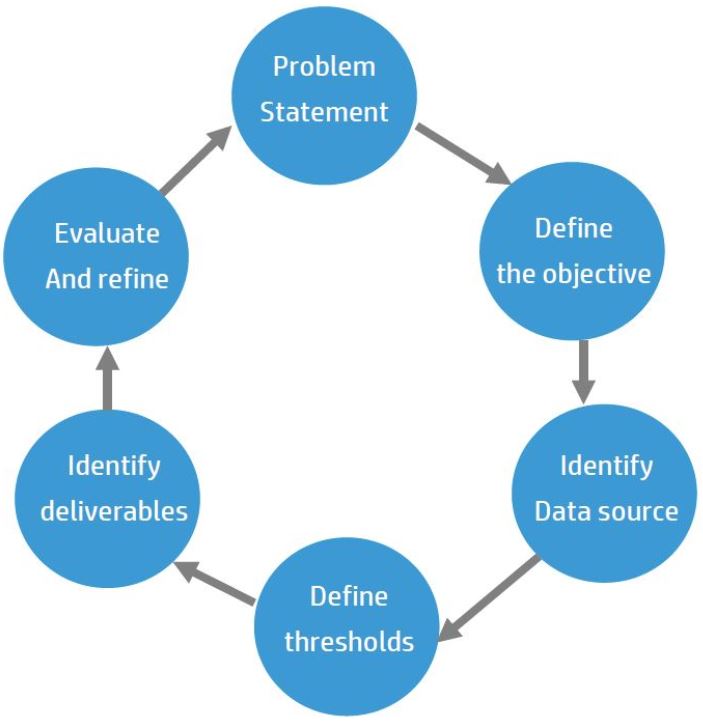
Use Case Lifecycle Model
This model is a more specific version of the previous use case model.
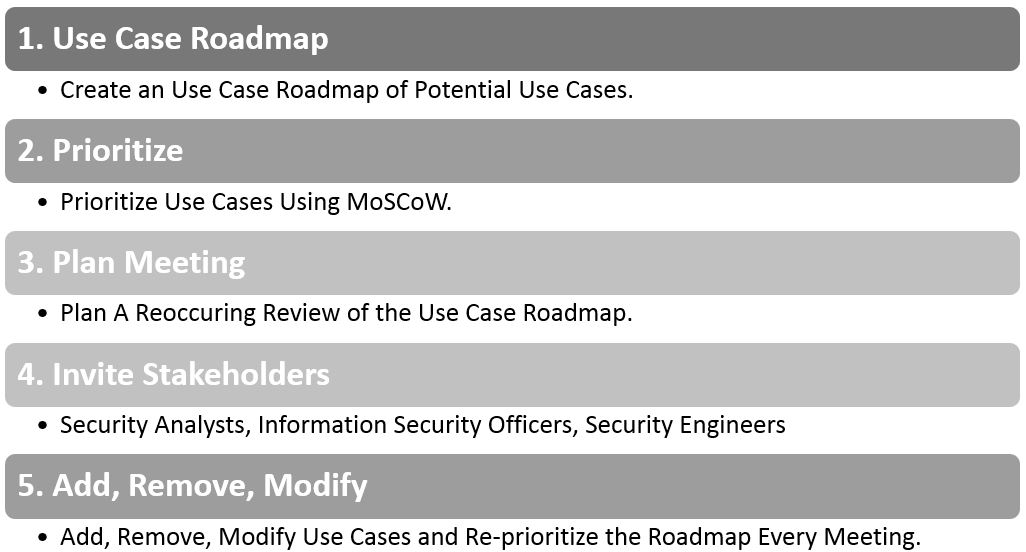
Use Case Roadmap Maintenance Process
This model is the most practical for maintaining your roadmap and keeping it relevant to outside threats.
Sources used for this article
The HP Attacker Lifecycle Methodology
http://www8.hp.com/h20195/v2/GetDocument.aspx?docname=4AA4-9490ENW
Lockheed Martin's Intel Driven Defense Whitepaper
http://www.lockheedmartin.com/content/dam/lockheed/data/corporate/documents/LM-White-Paper-Intel-Driven-Defense.pdf
The SANS whitepaper
http://www.sans.org/reading-room/whitepapers/auditing/successful-siem-log-management-strategies-audit-compliance-33528
HP Protect 2014 presentation: Arcsight Activate Framework
TB3267 - ArcSight Activate Framework - Petropoulos
HP Protect 2014 presentation: Data makes the difference
TT3052 - HP ArcSight Data makes the difference - Mitchell Webb John Rouffas
HP Protect 2014 presentation: threat modeling
BB3173 - Threat modeling Kill chains, diamond models, and the 50-yard line - Angela Gunn